The master’s theses defences of the Cybersecurity MSc programme (IVCM) taught jointly by TalTech and the University of Tartu will take place from May 27-29, on-site (TalTech room ICT-315) and over Teams.
27. May
Time: 10:00
Student: Riin Tamme
Title: CLOSED DEFENCE: Estonia’s Public Sector Awareness of Adversary Information Operations
Supervisor: Adrian N. Venables
Reviewer: Rain OttisTime: 11:00
Student: Britta Sillaots
Title: Convergence of Hospital and Consumer Wearables, Their Legal Aspects, and Micro Data Sovereignity
Supervisor: Matthew Sorell, Aleksi Kajander
Reviewer: Pavel TšikulTime: 11:40
Student: Anna Mandrenko
Title: Analyzing Drone Flight Logs for Forensic Behaviour Reconstruction
Supervisor: Matthew Sorell
Reviewer: Toomas LepikPAUSE 40 min
Time: 13:00
Student: Gerd Kukemilk
Title: Design and Implementation of a Configuration Management Database Compatible with ITIL and E-ITS
Supervisor: Toomas Lepik, Thomas Lepik
Reviewer: Olaf MaennelTime: 13:40
Student: Felix Nicolas Waschke
Title: Forensic Analysis of the Slack Web Application
Supervisor: Pavel Tšikul
Reviewer: Matthew SorellTime: 14:20
Student: Valerii Gakh
Title: Performance Comparison of Early Prompt Injection Detection Solutions
Supervisor: Hayretdin Bahsi
Reviewer: Olaf MaennelTime: 15:00
Student: Martin Mihalovic
Title: Genetic Malware Analysis
Supervisor: Alejandro Guerra Manzanares
Reviewer: Toomas Lepik28. May
Time: 10:00
Student: Muhammed Erbas
Title: Application of PASTA Threat Modeling to ECDIS in Autonomous Ships for ENhanced COLREG Compliance
Supervisor: Olaf Maennel, Gabor Visky
Reviewer: Dan HeeringTime: 10:40
Student: Janno Jaal
Title: Threat Modeling for AI/ML Based Healthcare Systems
Supervisor: Hayretdin Bahsi
Reviewer: RehmanTime: 11:20
Student: Hua Zhong
Title: A Deep Learning Solution for Detecting Image-Based Phishing/Spam Emails
Supervisor: Sven Nõmm, Adrian Venables
Reviewer: Andri RiidPAUSE 40 min
Time: 12:40
Student: Kati Sein
Title: Cybersecurity-related Support Needs and Challenges Incurred by Informal Support: A Study Among Estonian Home USers
Supervisor: Stefan Sütterlin, Tanel Mällo
Reviewer: Kaido KikkasTime: 13:20
Student: Nadezda Semjonova
Title: Cybersecurity Culture in Academia: the Case of Tallinn University of Technology
Supervisor: Kaido Kikkas
Reviewer: Ricardo LugoTime: 14:00
Student: Joosep Parts
Title: Attack Pattern Assessment of Telepresence Robots in Healthcare Systems Context
Supervisor: Kaido Kikkas, Janika Leoste
Reviewer: Andrew RobertsTime: 14:40
Student: Helena Jäe
Title: The Evolution of Cyber Conflict on the Example of Estonia, Georgia and Ukraine
Supervisor: Kaido Kikkas
Reviewer: Adrian Venables29. May
Time: 10:00
Student: Laura Danilas
Title: The Impact of Quantum Technologies on NATO’s Security and Defence Posture
Supervisor: Adrian N. Venables, Joanna Sliwa
Reviewer: Kaido KikkasTime: 10:40
Student: Karl Tamberg
Title: Harnessing Large Language Models for Software Vulnerability Detection: A Comprehensive Benchmarking Study
Supervisor: Hayretdin Bahsi
Reviewer: Risto VaarandiTime: 11:20
Student: Liam Simonos Warren
Title: Analysis of CDOC 2.0 Protocols in ProVerif
Supervisor: Nikita Snetkov
Reviewer: Ahto BuldasPAUSE 40 min
Time: 12:40
Student: Taaniel Kraavi
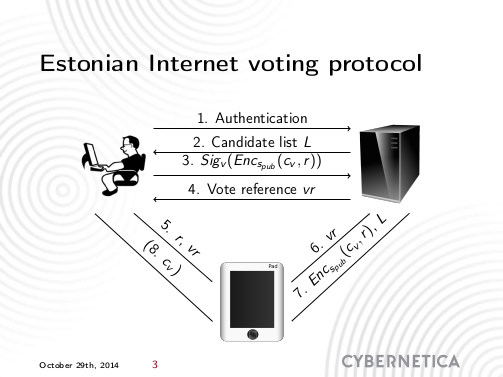
Title: Proving Vote Correctness in the Estonian Internet Voting System
Supervisor: Ahto Buldas, Jan Willemson
Reviewer: Jelizaveta VakarjukTime: 13:20
Student: Leonard Walter
Title: Evaluating the Use of MAQUE Proxies for Achieving DNS Privacy
Supervisor: Shaymaa Khalil, Silver Saks
Reviewer: Risto VaarandiTime: 14:00
Student: Diego Del Rio Manzanas
Title: Securing Remote Connectivity: A Systematic Penetration Testing Analysis of a Telepresence Robot
Supervisor: Shaymaa Khalil
Reviewer: Silver Saks
Links:
https://taltech.ee/en/events/masters-thesis-defence-cybersecurity-spring-semester-20232024