- [2023-03-16] I-voting in the 2023 Riigikogu elections (RK2023) took place from February 27th to March 4th. A new i-voting record was set with 313,514 votes (51%) being i-votes, meaning that i-voting has become the primary channel for voting. The biggest share of i-votes went to the Reform Party (above 60%). I-votes cast for EKRE and Center Party were around 30%. Several voting related incidents were observed and are covered below.
https://news.err.ee/1608904730/estonia-sets-new-e-voting-record-at-riigikogu-2023-elections
https://news.err.ee/1608905990/state-electoral-office-chief-no-election-complaints-filed-yet
https://news.err.ee/1608906230/online-voting-how-estonia-counts-and-secures-its-electronic-votes
https://news.err.ee/1608907502/expert-estonia-s-new-e-voting-record-no-surprise
https://news.err.ee/1608906014/online-votes-make-up-two-thirds-of-reform-less-than-third-of-ekre-votes - [2023-03-22] The State Electoral Office (RVT) published i-voting statistics. On average, 2’476 i-votes were cast every hour over six days. People were more active in the mornings and evenings. I-voting was most popular among Estonians in the 25-34 age group. The majority of votes were cast for more liberal parties.
https://news.err.ee/1608922322/online-voting-most-popular-among-estonians-aged-25-34
https://news.err.ee/1608922796/e-votes-spiked-in-final-hours-of-elections - [2023-02-27] I-voting started with two minor issues. The voting application was published with a 4-minute delay (09:04) and due to human error, at first, the days counter on the valimised.ee website wrongly displayed that i-vote can be cast after 37 days.
https://digi.geenius.ee/rubriik/uudis/e-haaletamine-algas-paari-vaheolulise-viperusega/ - [2023-02-27] On the first day of i-voting, around 7’500 updates in the voter list failed to timely reach the i-voting system. Apparently, the fault emerged as the cronjob was set to execute every 15 minutes, but since there were too many changes to apply, the cronjob did not complete before the process was restarted. As a result, 63 voters cast an i-vote in the wrong electoral district. At first RVT stated that these i-votes are valid, but later decided to cancel them. The affected voters were notified by email asking them to revote. In the middle of the voting period 50 voters had re-voted, the remaining 13 voters were notified again via SMS. However, 3 of the voters did not revote and their i-votes were removed from the ballot box before tallying the i-votes. This created a precedent, because these 3 i-votes were removed from the ballot box based on a non-verified assumption that the corresponding cryptograms contain an invalid candidate number. These votes should have been left in the ballot box where they would be verified and declared invalid during the tallying process.
https://news.err.ee/1608898568/voter-roll-updates-not-in-system-by-start-of-online-voting-monday-morning
https://news.err.ee/1608901154/commission-cancels-e-votes-cast-by-people-voting-at-former-addresses
https://www.err.ee/1608901067/valimiskomisjon-tuhistab-vanas-ringkonnas-e-haaletanute-haaled
https://digi.geenius.ee/rubriik/uudis/valimisteenistus-ei-avastanud-e-haaletuse-viga-ise-vaid-selle-tuvastasid-valijad/
https://www.valimised.ee/et/varske-valijate-nimekirja-info-joudis-e-haaletamise-susteemi-viibega
https://twitter.com/ikubjas/status/1630201509911711744
https://www.riigikogu.ee/download/0675f899-d955-4710-ad69-39d3137f84ce
https://www.riigikohus.ee/et/lahendid/?asjaNr=5-23-11/2
https://twitter.com/VotingVillageDC/status/1692032271791034603 - [2023-03-06] The Chairman of EKRE announced that i-voting is not serious and that EKRE will contest the i-vote in court unless it is made public how the votes came in, where they come from and how they were counted. EKRE submitted a request to RVT asking for all i-voting system logs as well as information about the developers and persons that have access to the i-voting system. RVT provided some names of the persons involved and offered EKRE auditors to recount the votes. However, logs containing personal data cannot be disclosed.
https://news.err.ee/1608905354/helme-e-voting-not-serious
https://news.err.ee/1608905744/ekre-vice-chair-curious-estonia-only-european-state-to-put-faith-in-e-vote
https://news.postimees.ee/7726546/ekre-submits-request-for-information-about-e-voting-system-to-state-electoral-office
https://news.err.ee/1608906380/justice-chancellor-audit-reports-show-no-problems-with-e-voting
https://digi.geenius.ee/rubriik/uudis/ekre-tahab-tutvuda-e-valimiste-logidega-mille-avaldamine-ei-ole-seadusega-kooskolas/
https://digi.geenius.ee/rubriik/uudis/valimisteenistus-on-valmis-ekre-jaoks-e-haali-uuesti-ule-lugema/
https://digi.geenius.ee/rubriik/uudis/ekre-vaidlustas-ametlikult-e-valimiste-tulemused/
https://digi.geenius.ee/rubriik/uudis/valimisteenistus-lubab-ekre-l-oma-audiitoritega-e-valimisite-susteemi-kontrollida/
https://news.err.ee/1608914084/committee-finds-ekre-leader-rights-not-infringed-at-riigikogu-election - [2023-03-09] EKRE appealed to the Supreme Court with a request to declare the result of the i-voting invalid. The main argument of the appeal is that i-voting is unconstitutional as the entire i-voting process is not described in the law. The Supreme Court later dismissed the complaint.
https://news.err.ee/1608909179/ekre-appeals-e-vote-result-at-supreme-court
https://news.err.ee/1608910829/martin-helme-we-are-protecting-constitutional-order-in-estonia
https://news.err.ee/1608909464/lawyer-riigikogu-election-e-vote-unconstitutional-and-cannot-be-counted
https://www.err.ee/1608909122/ekre-taotleb-riigikohtult-e-haaletuse-tulemuste-tuhistamist
https://www.err.ee/1608909278/keres-e-haali-ei-saa-arvestada-kuna-need-on-kokku-loetud-pohiseaduse-vastaselt
https://news.err.ee/1608911129/estonia-s-supreme-court-rejects-ekre-s-e-voting-election-complaint
https://www.riigikohus.ee/et/lahendid?asjaNr=5-23-8/2 - [2023-01-13] According to RVT, starting from the RK2023 election, voters voting in the polling station should be informed if an i-vote has been cast in their name. However, two experiments organized (by the author of this blog post) in polling stations in Tartu show that polling station workers do not inform voters and do not even know where such information can be seen in the election information system. This means that in practice, paper voters do not have means to detect that someone has cast an i-vote in their name.
https://digi.geenius.ee/rubriik/uudis/martsikuistel-valimistel-selgub-kas-e-valimiste-kuulujuttudel-on-alust/ - [2023-03-08] Dissatisfaction was expressed about the fact that i-voting results were published 3 hours after the end of the voting period. All together: there was a 40-minute delay for finalizing the list of voters; the invalidation of i-votes replaced by paper votes required 45 minutes; and the i-vote tallying process took an entire hour. RVT plans to acquire faster hardware to speed up the tallying process in the future.
https://digi.geenius.ee/rubriik/uudis/europarlamendi-valimiste-e-haaled-peaksid-saabuma-oluliselt-kiiremini/
https://twitter.com/ikubjas/status/1632499854160134145 - [2023-02-28] Allegedly, the Estonian United Left Party (EÜVP) asked its supporters to share photos of their ballot or i-vote, supposedly to protect against election fraud. The Electrocal Commission received several complaints and reminded the public that pressuring people to reveal their voting choices is against the law.
https://news.err.ee/1608899990/election-commission-tells-voters-to-stop-sharing-ballot-photos - [2023-03-03] The national broadcasting news program showed a video segment of the President of Estonia casting his i-vote. The vote verification QR code was not hidden and was visible in the video. RVT did not provide a comment on whether someone was able to successfully verify the vote (in the 30 minute period after the vote was cast) and thereby was able to break the secrecy of the President’s i-vote. This case illustrates that the i-voting application fails to communicate to the voter that the QR code is sensitive data and should not be disclosed to others.
https://digi.geenius.ee/rubriik/uudis/ajakirjanikel-oli-teoreetiline-voimalus-president-alar-karise-e-haale-salajasuse-murdmiseks/ - [2023-03-03] A man in Viljandi was dissatisfied with the organization of voting and left the polling station holding his ballot paper. Threats to call the police did not stop the man. Polling station staff contacted the police citing section 163 of the Penal Code, but the police declined to investigate the incident, saying no crime had been committed. We note that ballot papers that have been taken from polling stations introduce a risk since they can be used to enable different forms of vote buying (e.g., chain voting).
https://news.err.ee/1608903719/electoral-law-tested-as-viljandi-man-walks-off-with-ballot-paper
https://sakala.postimees.ee/7723786/valimissedeliga-putku-pannud-mees-joudis-politsei-huviorbiiti - [2023-03-05] Due to human error, one voter was able to vote twice. An employee of a polling station in Lasnamäe issued a ballot paper to the voter, even though the election information system contained information that the voter had already voted. The polling station employee confused the right to vote with the vote that was already given. It is not known in how many polling stations the voter tried to re-vote until he succeeded, but this incident clearly shows that the new election information system is confusing to the polling station employees, and hence such fraud is likely to succeed in a much larger scale. The police initiated misdemeanor proceedings according to the Penal Code in respect to election fraud and the person was fined 240 euros. A similar incident was reported from Kohtla-Järve, but there it turned out that the person went to vote a second time, thinking that he could vote for his ward on the basis of a power of attorney. As there was no reason to suspect malice, in this case misdemeanor proceedings were not initiated.
https://digi.geenius.ee/rubriik/uudis/uks-valija-sai-jaoskonnas-kaks-korda-haaletada-amet-valistab-infosusteemi-vea/
https://digi.geenius.ee/rubriik/uudis/kaks-korda-valimistel-haaletanud-inimene-sai-valimispettuse-toimepanemise-eest-trahvi/ - [2023-03-01] Estonian digital rights activist Märt Põder published a self-made vote verification application, which can be used to download and inspect the encrypted vote.
https://github.com/infoaed/kryptogramm
https://www.err.ee/1608901955/mart-poder-suuname-tahelepanu-demokraatia-opsusteemile
https://gafgaf.infoaed.ee/en/posts/perils-of-electronic-voting/ - [2023-03-08] Märt Põder was able to cast an i-vote by manually constructing the respective i-voting API requests from Linux command line. Since he only managed to submit the i-vote in the last minute of the i-voting period, he was not able to verify whether his submitted vote can be correctly decrypted using the vote verification application. Therefore, it is very likely that his vote contained an invalid cryptogram and hence this was the i-vote that was declared invalid in the vote tallying process. RVT announced that they will not investigate who cast the invalid i-vote as that would not be in line with the principle of election secrecy.
https://gafgaf.infoaed.ee/en/posts/perils-of-electronic-voting/
https://p6drad-teel.net/~p6der/evote-log.html
https://digi.geenius.ee/eksklusiiv/digiaktivist-andis-e-valimistel-isetehtud-koodireaga-haale/ - [2023-02-15] During the i-vote encryption key generation process, the i-voting observer Märt Põder requested to ensure that the Windows 10 machine used to generate the private key did not contain malware that could generate a weak key or leak the private key. Märt Põder submitted an official complaint asking RVT to make a copy of the machine’s hard disk available for inspection. In their answer, RVT explained that the inspection of the hard disk did not guarantee absence of malware, e.g., in computer memory or in other components. However, the complaint was partially satisfied by allowing the inspection of the hard disk copy in the premises of RVT.
https://www.riigiteataja.ee/akt/328022023004
https://www.postimees.ee/7719324/valimiskomisjon-rahuldas-soovi-uurida-e-haaletamise-susteemi-kovaketast
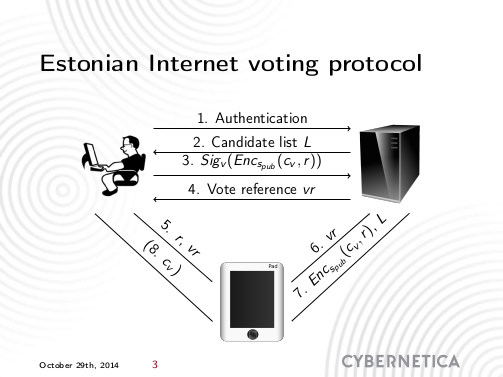
https://twitter.com/trtram/status/1625837567433220097 - [2023-03-24] Märt Põder demonstrated a method showing how a person can reliably prove to third parties the content of the i-vote cast by the person and also prove that this i-vote went into the final tally (i.e., was counted). First, using a custom built vote verification application and the QR code shown after casting the vote, the voter’s vote is retrieved from the vote collector server and decrypted. The vote registration receipt attached to the vote proves that the vote was received by the vote collector server. To prove that this was the last i-vote cast by the person, the person can request digitally signed logs of ID-card/Mobile-ID certificate revocation requests from SK ID Solutions AS. These logs will show the time of the last certificate validity query made by the vote collector server, proving that re-voting did not take place. To prove that the i-vote was not canceled by a paper vote, a digitally signed statement from RVT can be obtained which will answer whether the voter’s i-vote or paper vote was counted in the election.
https://youtu.be/vWMaoqPY2-M
https://infoaed.ee/proof2023
https://infoaed.ee/salajasus/eksperthinnang.pdf
https://digi.geenius.ee/rubriik/uudis/valimisteenistus-seletab-lahti-miks-digiaktivisti-vaiteid-e-haale-salajasuse-murdmise-osas-ei-vasta-toele/
https://gafgaf.infoaed.ee/posts/usaldada-valetamisteenistust/ - [2023-04-06] Märt Põder discovered that the content of i-votes cast in RK2023 does not comply with the technical requirements established by the election commission. In particular, although the decision requires that the EHAK code of the administrative unit must be included in the encrypted ballot, in reality the voting app set it to 0000. While in practice the EHAK code is not required to count the votes, strictly speaking, such votes do not meet the requirements and therefore should be declared invalid and discarded in the tallying process. A similar non-compliance was discovered regarding the digital signature containers constructed by the official voting application. In particular, that they lack signature verification data and show up as invalid when opened with the official DigiDoc client (however, validation data is added by the server and hence a proper signature container should be available on the server side). Märt Põder submitted a complaint, but it was rejected due to being submitted after the deadline. A crime report was submitted to police, but the police has refused to initiate the proceedings. An appeal is currently being processed by the administrative court and an application has been submitted to the European Court of Human Rights.
https://www.riigiteataja.ee/akt/312102022001
https://gafgaf.infoaed.ee/posts/kolmas-lugemine/
https://gafgaf.infoaed.ee/posts/kehtetute-sedelite-valitsus/
https://gafgaf.infoaed.ee/posts/juurkaebus-2023/
https://digi.geenius.ee/rubriik/uudis/ronald-liive-ekre-l-ja-riigikohtu-esimehel-on-oigus-e-valimised-vajavad-tosist-reguleerimist/
https://digi.geenius.ee/rubriik/uudis/e-valimised-jalle-kohtus-vaatleja-nouab-e-haalte-ebaoige-lugemise-osas-kriminaalmenetlust/
https://twitter.com/trtram/status/1687392928618909696 - [2023-04-23] According to a complaint by Märt Põder, in RK2023 an i-vote cast in the last minute could only be verified for 15 minutes rather than 30 minutes as prescribed by the regulation. According to RVT, the i-voting system is shut down 15 minutes after the end of the i-voting period. The current i-voting system does not support a feature where the vote collector would stop accepting new i-votes but would still allow the last votes to be verified.
https://digi.geenius.ee/rubriik/uudis/e-valimiste-haalekontroll-lulitati-liiga-vara-kinni/ - [2023-03-01] A group of election observers led by Märt Põder, issued a joint statement and petition demanding i-voting to be made observable, proposing five specific legal and procedural changes in order to achieve that. In particular, the proposal is to: (1) provide legal means for observers to file complaints based on their observations; (2) make it possible to observe the voting processes from their first step to the last; (3) each IT-related i-voting activity must be made legally contestable; (4) the dispute period for i-voting must be extended; and (5) all i-voting related materials and documentation must be made available to observers for familiarization early in the process.
https://rahvaalgatus.ee/initiatives/7b9ecdfa-3b56-45d4-a0f8-a52ced3e5803?language=en#initiative-header
https://vaatlejad.github.io/ - [2023-08-31] OSCE published their final report on RK2023. Among i-voting related recommendations: (1) election authorities should proactively address i-voting related concerns raised by entities that distrust i-voting (e.g., EKRE); (2) consider introducing cryptographic methods to prevent invalid ballots reaching ballot box; (3) improve quality assurance to avoid incidents such as the 63 voters who cast votes in an incorrect voting district; (4) the National Electoral Committee (VVK) should publish complete and up-to-date information and code concerning the i-voting system; (5) VVK should improve communication regarding the time that is required to count i-votes; (6) OCSE recommends implementing countermeasures against the attack described by Olivier Peirrera which would circumvent the vote verification process by a malicious voting app simulating an application crash; and (7) OSCE points out that in RK2023 the critical step of removing the re-votes was not audited – this should not happen again.
https://www.osce.org/odihr/elections/estonia/551251
https://digi.geenius.ee/rubriik/uudis/osce-tahab-et-eesti-e-valimised-oleksid-rohkem-auditeeritavad/ - [2023-09-14] Even though the Supreme Court dismissed all RK2023 election complaints, in a competing opinion the President of the Supreme Court (Villu Kõve) pointed out the challenges of assessing i-voting related complaints and drew attention to the fact that the regulation of i-voting needs to be written into the law more thoroughly than before. The Ministry of Justice has prepared legislative amendments, but VVK raises fears over impartiality, as the government would have more say in the organization of i-voting.
https://www.riigikohus.ee/et/lahendid?asjaNr=5-23-20/6
https://www.postimees.ee/7794592/intervjuu-riigikohtu-esimees-villu-kove-e-valimised-ei-saa-pohineda-vaid-usul
https://digi.geenius.ee/rubriik/uudis/riigikohus-jattis-ekre-ja-vasakpartei-valimiskaebused-rahuldamata/
https://news.err.ee/1608932273/supreme-court-dismisses-all-election-complaints
https://news.err.ee/1608933176/ekre-will-not-further-contest-march-5-riigikogu-election-result
https://www.delfi.ee/artikkel/120158604/ekre-laheb-e-haaletamise-vaidlustamisega-riigikohtus-uuele-katsele
https://news.err.ee/1608914885/electoral-committee-rejects-united-left-party-and-ekre-election-complaints
https://news.err.ee/1608919430/electoral-committee-rejects-ekre-election-complaint-filed-past-deadline
https://news.err.ee/1608920858/ekre-once-again-appeals-march-5-election-e-vote-with-supreme-court
https://digi.geenius.ee/rubriik/uudis/e-riigi-endine-peaarhitekt-e-valimiste-puhul-ei-ole-liigset-jaakriski-tuvastatud/
https://digi.geenius.ee/rubriik/uudis/president-karis-uuele-riigikogule-seadustes-peab-olema-kirjas-koik-oluline-mis-puudutab-e-valimisi/
https://news.err.ee/1608909215/andres-sutt-security-of-e-elections-has-always-been-a-top-priority
https://arvamus.postimees.ee/7862306/ago-samoson-e-valimised-on-praegu-usalduse-kusimus
https://news.postimees.ee/7807258/e-voting-rules-to-be-made-clearer
https://news.err.ee/1609024067/justice-ministry-sets-about-clarifying-e-voting-rules
https://news.err.ee/1609099541/amendment-to-electoral-law-raises-fears-over-impartiality
Other events (not related to RK2023):
- [2022-04-27] In 2022, the government allocated 4 million euros for i-voting. Half of it was designated to the development of the election information systems, additional security testing and organization of elections.
https://digi.geenius.ee/rubriik/uudis/venemaa-soda-ukrainas-suurendab-eesti-e-valimiste-kuberturvalisust/ - [2022-06-21] In 2022, MKM published the KPMG audit report on the security of the election information system and related processes. The audit did not analyze the security of i-voting protocols and its implementation/deployment. The audit found several issues: (1) there is no requirement to perform a security audit on the i-voting system; (2) problems in the risk assessment procedures; (3) the current ad-hoc funding method is not able to guarantee security and continuity of the i-voting system; (4) lack of basic testing before the election cycle. The audit found that from the 25 recommendations of the i-voting working group only 7 have been (somewhat) implemented.
https://twitter.com/ikubjas/status/1543746621527277568
https://digi.geenius.ee/rubriik/uudis/audit-leidis-e-valimistel-14-puudust-ja-mittevastavust-osade-realiseerumist-prognoositakse-jargmise-kolme-aasta-jooksul/
https://www.mkm.ee/uudised/audit-e-valimised-turvalised
https://www.mkm.ee/media/7414/download - [2023-01-17] In December, ITL and Tarvi Martens sent a letter asking VVK to enable i-voting using Smart-ID. According to VVK’s legal interpretation, enabling Smart-ID requires changes to the law. Tartu University researcher Arnis Paršovs, however, draws attention to the security risks of enabling Smart-ID in i-voting.
https://digi.geenius.ee/eksklusiiv/segadus-smart-id-ga-juba-seekord-oleks-e-valimistel-peaaegu-saanud-sellega-haalt-anda/
https://digi.geenius.ee/rubriik/uudis/smart-id-loonud-ettevotte-esindaja-oluline-on-et-inimesel-poleks-vahet-millist-eid-vahendit-ta-kasutab/
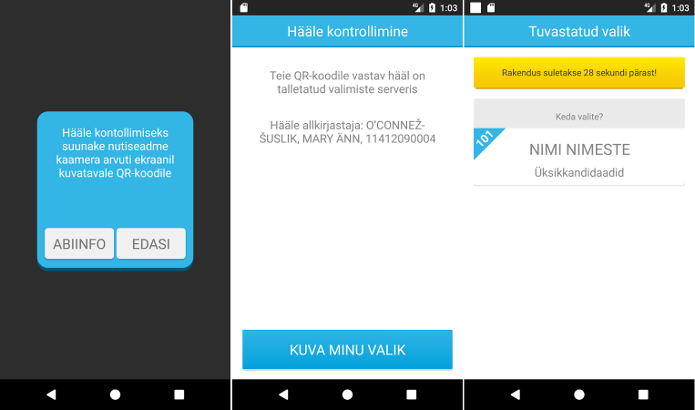
https://digi.geenius.ee/rubriik/uudis/siseministeeriumi-asekantsler-selgitab-miks-nad-ei-toeta-smart-id-lubamist-valimistel/ - [2023-09-29] RIA has tasked Cybernetica to create a prototype i-voting application for smartphones. The app has been developed and supports Mobile-ID and Smart-ID as the authentication means. The coalition agreement of the current government has established the goal to enable m-voting and the government is working to enable it for the EP2024 elections. RVT, however, considers introducing m-voting to be risky, mostly because of the Apple app store, where there is little control over the app’s distribution.
https://www.ria.ee/en/news/pilot-application-created-e-voting-smart-devices.html
https://digi.geenius.ee/rubriik/uudis/e-valimistest-voib-saada-moodanik-sel-aastal-valmib-m-valimiste-app/
https://digi.geenius.ee/rubriik/uudis/m-valimiste-api-turvalisuses-ei-ole-veel-veendutud/
https://digi.geenius.ee/rubriik/uudis/peagi-saab-uuesti-haaletada-kuid-nuud-juba-mobiiliga/
https://digi.geenius.ee/rubriik/uudis/fotod-m-valimiste-iosi-ja-androidi-appide-esialgne-disain-sai-valmis/
https://digi.geenius.ee/rubriik/uudis/riik-votab-m-valimiste-api-loomist-vaga-tosiselt-juba-on-kohtutud-appleiga/
https://valitsus.ee/en/coalition-agreement-2023-2027
https://www.err.ee/1608991649/valimiskomisjon-m-haaletuse-kasutamine-tooks-kaasa-liiga-palju-riske
https://mkm.ee/uudised/riisalo-siht-jargmisteks-valimisteks-luua-voimalus-haaletada-nutiseadmega
https://news.err.ee/1609078918/government-plans-to-allow-voting-by-smart-device-from-next-elections
https://news.err.ee/1609080746/doris-pold-m-voting-sure-to-boost-turnout
https://news.err.ee/1608992003/electoral-committee-m-voting-entails-too-many-risks
https://news.err.ee/1609108271/electoral-committee-chair-worth-keeping-with-times-but-m-voting-risky
https://news.err.ee/1609109348/legal-scholar-government-can-only-regulate-e-voting-technical-details - [2023-06-29] The Academy of Sciences established a cybersecurity commission who will examine election security. The commission includes Dan Bogdanov (head), Teet Raidma, Alo Einla, Arne Koitmäe, Kristjan Krips, Ivo Kubjas, Liisa Past, Mihkel Solvak, Ahto Truu, Tarmo Uustalu, Priit Vinkel and Jan Willemson. The desire of the committee members is to raise the quality of the discussion on the security of the e-state and to create supporting tools and models. As a kick-off event, the commission organizes a conference on trust and reliability to discuss the technological and social science aspects of election technology.
https://digi.geenius.ee/rubriik/uudis/teaduste-akadeemia-hakkab-uurima-valimiste-turvalisust/
https://www.akadeemia.ee/wp-content/uploads/2023/06/kuberturvalisuse-komisjoni-koosseisu-kinnitamine-2023.06.20_juh-prot-8_vv_%C2%A7-30.pdf
https://www.akadeemia.ee/en/events/conference-on-trust-and-reliability/ - [2023-03-23] Tartu County Court convicted Allain Karuse for vote buying in Valga at the KOV2021 elections. According to the charges, he promised two persons free diesel fuel – 10 liters in one case and 15 in the other. One person was offered at least €20 in cash. Another person was handed €70 who used it to buy meals for themselves and six other persons in a Valga restaurant. No information is available on whether and how it was ensured that the voters cast the vote for the particular candidate.
https://news.err.ee/1608924074/tartu-county-court-convicts-allain-karuse-of-vote-buying - [2022-10-27] The court found Narva politician (Sergei Gorlatš) guilty of vote buying and sentenced him to one year and eight months in prison. The indictment says that Gorlatš organized a trip for 40 people from Narva to Toila that included a tour, SPA visit and picnic. Later, the attendees were permitted to i-vote on Gorlatš’ laptop while still on the bus, among them 17 persons did so.
https://news.err.ee/1608767971/narva-politician-sergei-gorlats-found-guilty-of-vote-buying
Research articles:
- [2023-08-23] A research article by Tobias Hilt, Kati Sein (Cybernetica), Tanel Mallo (Cybernetica), Melanie Volkamer and Jan Willemson (Cybernetica): “Voter Perception of Cast-as-Intended Verifiability in the Estonian i-vote protocol”. The researchers performed semi-structured interviews with 13 voters to investigate the perception of individual verifiability in online elections in the aftermath of the 2013 parliamentary election in Estonia. The study finds that the voters clearly lack comprehension of the real purpose of the verifiability step (i.e., to detect a malware attack).
https://research.cyber.ee/~janwil/publ/voterperception.pdf
https://twitter.com/EVoteID/status/1709556280216412465/photo/1
https://twitter.com/trtram/status/1653773719960006657 - [2023-09-22] A research article by Jan Willemson (Cybernetica) and Kristjan Krips (Cybernetica/UT): “Estimating carbon footprint of paper and Internet voting”. The paper compares the carbon footprint of paper voting in polling stations with the emissions of i-voting in KOV2023. The results show that paper voting has about a 180 times higher carbon footprint, owing largely to the need to transport the voters to the polling stations and back.
https://research.cyber.ee/~janwil/publ/VotingCO2.pdf
https://link.springer.com/chapter/10.1007/978-3-031-43756-4_9 - [2022-10-01] A research article by Piret Ehin (UT), Mihkel Solvak (UT), Jan Willemson (Cybernetica) and Priit Vinkel (Cybernetica): “Internet voting in Estonia 2005–2019: Evidence from eleven elections”. The article examines Internet voting in Estonia over 15 years and 11 nation-wide elections.
https://www.sciencedirect.com/science/article/pii/S0740624X2200051X - [2022-09-24] A research article by Cornelia Sindermann, Dmitri Rozgonjuk (UT), Mihkel Solvak (UT), Anu Realo (UT) and Kristjan Vassil (UT): “Internet voting: the role of personality traits and trust across three parliamentary elections in Estonia”. The researchers investigated what affects the decision to use or not use internet voting. The work indicates that, out of the Big Five personality traits, it is only Agreeableness that seems to be related to trust in internet voting and the use of internet voting.
https://link.springer.com/article/10.1007/s12144-022-03644-4 - [2022-07-19] A research article by Jan Willemson (Cybernetica): “Towards Identifying Social Factors behind (In)Efficiency of Voting Security Measures”. In this article, the author analyzes various social factors that could explain why different countries implement different security measures in their voting systems. E.g., why in Switzerland coercion and vote buying is not part of the threat model, while voting systems in other countries try to implement measures against these attacks.
https://www.jedem.org/index.php/jedem/article/view/673 - [2022-06-08] Kristjan Krips (Cybernetica/UT) defended his PhD thesis “Privacy and coercion resistance in voting”. Among other things, the work contains a great amount of information about the Estonian i-voting system. The work indicates that the attack resistance of paper voting tends to be overestimated, while the Estonian internet voting system could also be improved.
https://ut.ee/en/node/138599
https://kuku.pleier.ee/podcast/kuue-samba-taga/132123
https://novaator.err.ee/1608635968/doktoritoo-e-haaletamise-kontrollitavusele-seab-piirid-haalteostmise-risk - [2022-06-06] A research article by Maris Vutt (UT): “Electronic Voting in Adopting Resolutions of Limited Companies: The Example of Estonian Law”. The article provides an overview of how Estonian companies implement electronic voting in shareholders’ meetings. The author finds that although the law contains no precise requirements, it should be taken into account that the procedure laid down for electronic voting must ensure the identification of shareholders as well as the security and reliability of electronic voting.
http://dx.doi.org/10.13165/j.icj.2022.06.007