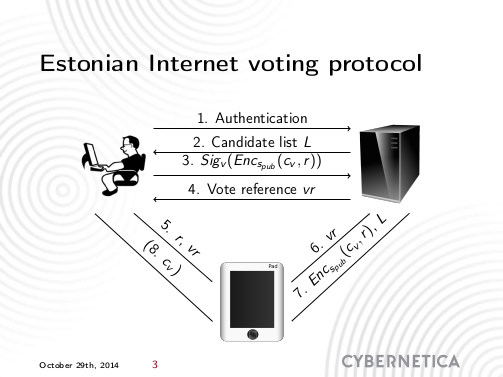
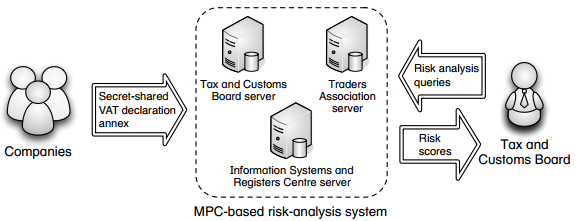
The focus of this Yearbook is on criminal procedure with special emphasis on surveillance operations. There are three articles that are of our interest.
“Supervision over surveillance”, Uno Lõhmus, Visiting Professor at the University of Tartu:
In conclusion
First, full judicial pre-approval of surveillance operations, judicial supervision of the operations at the time of conduct thereof, and effective review of the operations after their completion are not ensured. Second, the rules on surveillance are laconic, incomplete and ambiguous, and the case law has not been able to improve this situation. In other words, legal clarity of the law is not ensured. This adds to the complexity of judges’ work and may also contribute to superficiality.
…
In addition, the case law does not clarify whether the installation of spyware in a computer system should be regarded as the installation of a technical means.
…
As of 1 January 2013, examination of traffic and location data in electronic communication is not considered to be a surveillance operation.
“Problems related to surveillance – the perspective of a defence counsel”, Küllike Namm, attorney-at-law:
In conclusion
This article focuses on the questions that have arisen in connection with surveillance operations and to which the current law does not provide answers. The discussion of these issues is intended to point out that the activities of public authorities in organising surveillance are inadequately regulated by the Code of Criminal Procedure. This creates a situation where the provisions on access to information on surveillance operations do not guarantee that a person subjected to surveillance can examine the data collected by surveillance operations and, where necessary, take possession of the data in a format that can be played back.
“Some problems encountered in computer system searches”, Eneli Laurits, Adviser to the Penal Law and Procedure Division of the Ministry of Justice:
Summary
The Code of Criminal Procedure of Estonia does not regulate computer system searches. It is relatively difficult to apply the existing rules to the collection of evidence in the manner described in this article, but it is still possible.
…
When performing an inspection, the body conducting proceedings is not entirely free of jurisdiction-related issues: for example, if the object of inspection is the social media website of a victim or a suspect, then the inspection of the website is complicated in theory, but simple in practice – a mouse click is enough to display various data within the territory of Estonia. An inspection can be based on cooperation (the subject voluntarily provides the user IDs and passwords), but there is always the possibility that voluntary cooperation fails. An investigative body should be able to rely on a legal regime in such cases.
Links:
http://www.riigikohus.ee/vfs/2071/Riigikohtu_aastaraamat_eng_veebi.pdf