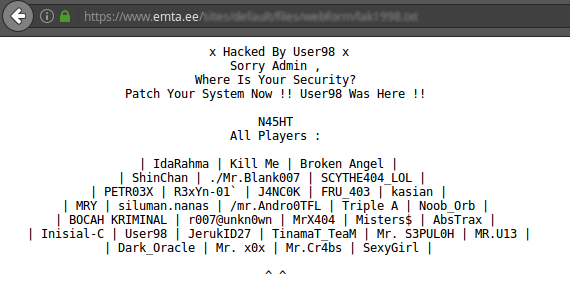
Estonian web security agency WebARX detected in their logs that hackers, apparently originating from Indonesia, had managed to find a security hole in the website of Estonian Tax and Customs Board and added there a file.
“If you look what has been posted in User98 Deface.id page, you can see that the hack of Estonian Tax and Customs Board website was in fact pure coincidence. On the same day, January 17, User98 attacked in total 72 websites. All websites were using the content management system Drupal, and in all of these sites the uploaded file lak1998.txt had identical content” said Oliver Sild, CEO of WebARX.
Tax and Customs Board spokesman Rainer Laurits said that calling the incident a hacking attack is an exaggeration. According to him, the administrator of website allowed users to write comments. Using the functionality provided, the text file was uploaded. “Unsuitable items we removed, including the post in question. In reality, no danger was caused to emta.ee website.”
Running unpatched CMS asks for trouble.
Oliver Sild, CEO of WebARX, who brought the incident to Postimees attention, in his website esec.ee offers security related services, such as restoration of hacked sites and masshack prevention.