- [2018-07-06] There are plans to simplify application for Mobile-ID. Currently, to enable Mobile-ID the person has to authenticate in PPA web environment. In the future this security feature will be implemented using face recognition. The solution is developed with MindTitan.
https://www.err.ee/844674/mobiil-id-taotlemine-lihtsustub - [2018-07-06] RIA temporary removed banklink authentication from eesti.ee due to some vulnerability being found in the implementation of authentication mechanism.
https://www.err.ee/844496/ria-on-tanavu-avastanud-mitu-tosist-turvanorkust - [2018-07-03] New version of DigiDoc 4 client has been released. The changes are mainly in the frontend. The functionality of DigiDoc3 Client, DigiDoc Crypto and ID card utility is now merged in a single application.
https://www.err.ee/843839/uus-id-kaardi-rakendus-digidoc-4-jouab-arvutitesse - [2018-06-29] It is now possible to order test cards of new generation ID card chips. New generation will be introduced in identity documents in the end of 2018. While the software and drivers are available, the technical documentation is not yet public. The card will also have a contactless interface, but not clear yet what functionality will be accessible over it.
https://www.ria.ee/ee/rialt-saab-susteemide-testimiseks-tellida-uue-id-kaardi-testkaardi.html
https://www.err.ee/843133/tanavuse-aasta-lopus-tuleb-valja-kontaktivaba-liidesega-id-kaart - [2018-06-27] The maintenance of ID card helpline moves from AS SK ID Solution to Tieto Estonia AS. The new helpline will have new number, but will not provide support 24/7.
The certificates can be suspended 24/7 calling SK ID Solutions using the current number.
https://www.ria.ee/en/the-id-card-helpline-number-will-be-changed-on-sunday.html
https://news.err.ee/842614/ria-changing-id-card-helpline-number-scaling-down-user-support - [2018-06-22] Government discussed the results of implementing cybersecurity strategy 2014-2017. The report shows that 70% of the activities were completed, 16% of the activities were completed in the next period, and 14% of the activities were either not completed mainly due to lack of financial or human resources.
http://www.ituudised.ee/uudised/2018/06/22/kuberturvalisuse-edendamisel-mitmeid-kitsaskohti - [2018-06-22] CyberSpike 2018 has finished and winners are known: 1st place – Artur Luik (TUT), 2nd place – Georg Kahest (TUT), 3rd place – Martin Širokov (Tallinn Technical Gymnasium).
https://geenius.ee/rubriik/teadus-ja-tulevik/eesti-noored-panid-oma-kuberkaitseoskused-proovile-kaitstes-lumemaad/ - [2018-06-18] Tõnu Tammer is the head of Estonian CERT from the beginning of June 2018. Interview (in Estonian):
https://geenius.ee/uudis/certi-uus-juht-mullu-kollitas-lunavara-tanavu-pannakse-ohver-oma-teadmata-kruptoraha-kaevandama/
https://geenius.ee/uudis/eesti-cert-sai-uue-juhi/ - [2018-06-15] Geenius has analyzed transparency reports of biggest service providers for information requests from Estonian state authorities. Google has received requests about 85 user accounts, delivered data 75% of cases. No requests received by Apple. Microsoft has received requests for five user accounts. Facebook received request for 143 users, delivered data in 67% cases. No data requested from Twitter.
https://geenius.ee/uudis/suur-ulevaade-tehnoloogiafirmadelt-noutakse-endiselt-palju-eestlaste-andmeid/ - [2018-06-14] CyCon 2018 videos of keynotes and panels are online:
https://www.youtube.com/watch?v=G0SRPC0Etv0&list=PLV8RTnZwQxcmJQGPlyxknrsVArsUNx1oE - [2018-06-13] National Audit Office has done some audits in Estonia’s local governments and have found that IT security requirements still aren’t implemented.
https://news.err.ee/839106/local-councils-it-security-entirely-inadequate-national-audit-office-finds
https://www.riigikontroll.ee/Riigikontrollipublikatsioonid/Auditiaruanded/tabid/206/Audit/2466/Area/1/language/et-EE/Default.aspx - [2018-06-11] Estonian man arrested for stealing Bitcoin wallets by accessing victim’s e-mail accounts. Large database of user account credentials found on the suspect’s computer.
https://geenius.ee/uudis/kahtlus-eesti-mees-teenis-bitcoine-varastades-mitu-miljonit-eurot/ - [2018-06-11] Estonian criminal police has added databases of compromised user accounts found in their investigations to the publicly searchable service “Have I Been Pwned” which will help the victims to get informed.
https://geenius.ee/uudis/politsei-kontrollige-ega-teie-kontot-pole-ule-voetud-ega-bitcoine-varastatud/
https://www.troyhunt.com/data-provided-by-the-estonian-central-criminal-police-is-now-searchable-on-have-i-been-pwned/ - [2018-06-08] The state supports UT and TUT cyber security studies with 1.5 millions. The universities are expected to open up research teams for cryptography, digital expertise and cyber defense.
http://www.ituudised.ee/uudised/2018/06/08/riik-toetab-tu-ja-ttu-kuberkaitse-opet-15-miljoniga - [2018-06-08] Swedbank implements limitations for code card use in internet banking. From February 2019 code cards will be abandoned. Currently around 200 000 users are using password card.
https://tehnika.postimees.ee/4501277/swedbank-asus-paroolikaarte-kaotama
https://tarbija24.postimees.ee/4486778/paroolikaardi-kasutajate-arv-vaheneb-visalt-200-000-swedbanki-klienti-jatkuvalt-kasutab-seda - [2018-06-06] RIA’s “Annual Cyber Security Assessment 2018” has been translated to English. Section about ROCA flaw and Internet voting included.
https://www.ria.ee/en/head-of-ria-last-year-was-proof-that-securing-the-digital-lifestyle-requires-investing.html
https://www.ria.ee/public/Kuberturvalisus/RIA-CSA-2018.pdf
https://www.ria.ee/ee/ria-esitles-kuberturvalisuse-aastaraamatut.html - [2018-06-01] Vulnerability has been found in AS Ühisteenused self-service portal parkimine.ee. The flaw allows to browse parking tickets issued to other persons by changing ID in the URL.
https://geenius.ee/uudis/turvaauk-uhisteenuste-veebist-sai-igauks-naha-teiste-inimeste-ja-soidukite-andmeid/
https://geenius.ee/uudis/anto-veldre-uhisteenuste-trahviveebist-leitud-turvaauk-on-muldvana-nii-et-kuidas-see-sinna-sattus/ - [2018-05-24] National Audit Office has identified problems with critical state databases: they lack risk analysis, action plan, only minimum needed audits are conducted, backups have not been tested, but no reason to panic.
https://news.err.ee/834127/national-audit-office-identifies-weaknesses-in-critical-database-care - [2018-05-24] Anto Veldre published harsh opinion article in the response to the seminar held by National Electoral Committee about the possibility to introduce i-voting using mobile device.
https://geenius.ee/uudis/anto-veldre-mobiilihaaletamine-saab-tulla-ainult-ule-minu-laiba/ - [2018-05-23] RIA is performing security assessment of Smart-ID to decide whether it should be allowed for authentication to state services.
https://www.err.ee/833840/turvatesti-labimisel-voib-ka-smart-id-st-saada-riigiteenuste-autentimisviis - [2018-05-17] It has been found that ID card manufacturer Gemalto has generated private keys outside the chip. As a result, PPA is recalling 12’500 ID cards and revoking the affected certificates on 2018-06-01. Gemalto denies accusations.
https://news.postimees.ee/4490059/estonia-replacing-12-500-unsecure-id-cards-for-free
https://news.postimees.ee/4491312/new-id-card-fault-could-have-been-intentional
https://news.err.ee/832236/police-12-500-id-card-certificates-to-be-deleted-due-to-security-issue - [2018-05-10] RIA has published TUT study about lessons learned from the ID card case. The translation to English is in progress.
https://www.ria.ee/public/PKI/ID-kaardi_oppetunnid.pdf
https://news.err.ee/822819/ttu-cybersecurity-center-director-estonia-needs-more-specialists
https://geenius.ee/uudis/uuring-id-kaardi-kriisile-oleks-olnud-kiire-lahendus-kui-info-selle-kohta-eestisse-oleks-joudnud/
https://www.err.ee/822535/rain-ottis-id-kaardi-kriisist-eestis-on-vaja-spetsialistide-reservi
https://www.err.ee/822452/ttu-raport-kritiseerib-id-kaardi-kriisi-valguses-eesti-hadaolukordade-plaane - [2018-04-25] State will allocate 1.1 million to RIA to cover expenses due to ID card crisis.
https://majandus24.postimees.ee/4478455/valitsus-plaanib-id-kaardi-kriisi-tottu-ria-le-eraldada-ule-miljoni-euro - [2018-04-19] RIA managed to factor one vulnerable RSA authentication key to prove that the ROCA flaw was not only a theoretical threat and the steps taken to eliminate the risk were justified. The factorizing software was provided by Cybernetica AS. Not known how much processing resources the attack required.
http://epl.delfi.ee/news/eesti/id-kaart-murti-lahti-ria-toestas-et-kara-id-kaardi-turvanorkuse-parast-polnud-asjata?id=81807683 - [2018-04-11] Digi-ID validity term will be extended from 3 to 5 years.
https://geenius.ee/uudis/digiisikutunnistus-ehk-digi-id-kehtib-nuud-varasemast-kauem/
https://tarbija24.postimees.ee/4481983/digi-id-kehtivusaeg-pikenes-viiele-aastale - [2018-03-26] Police has posted a job offer which involves solving puzzle of cat GIF.
https://geenius.ee/uudis/kui-suudad-selle-kassi-gifi-moistatuse-lahendada-ootab-sind-eestis-haruldane-toopakkumine/ - [2018-03-23] RIA has announced EUR 150k worth procurement for design of new eID logos.
https://geenius.ee/uudis/ria-tellib-150-000-euroga-e-id-visuaalse-segapudru-asemele-uue-valimuse/ - [2018-03-23] Geenius has listed what data by law the law enforcement agencies in Estonia can ask from mobile operators and Internet service providers:
https://geenius.ee/uudis/millised-sinu-kohta-kaivad-andmed-politsei-su-telefonioperaatori-kaest-katte-saab/ - [2018-03-20] The videos from Nordic-Baltic Security Summit 2018 are online. Some selected presentations:
Andres Elliku – CERT-EE S4A: an Open-Source Solution for Distributed Network Security Monitoring
Merike Käo – Estonian 2007 and 2017 Incidents – Have We Learned to Respond Better?
Elsa Neeme – Estonian Cyber Security Act – Ensuring Public Order In Cyber Domain
Rain Ottis – Selected lessons from the 2017 ID-Card case
Oskar Gross – What are the Challenges of Handling Cyber Crime?
https://tehnika.postimees.ee/4444549/otse-kaljurand-koppel-keskkriminaalpolitsei-ja-teised-kogu-tode-kuberturvalisusest
https://summit.confent.com/summary18/ - [2018-03-05] According to the head of cybercrime bureau Oskar Gross, secure encryption capability improves the security for ordinary users. The technological environment has not caused a particular headache for PPA in solving crimes.
https://novaator.err.ee/687558/ppa-kruptorakendustest-krupteeritud-sideta-oleks-internet-ohtlikum-koht - [2018-02-13] Due to human error on mobile operator Elisa side, emergency line 112 could not be reached for several hours. In total 151 persons were affected. SMIT discovered the error and Elisa fixed it in 20 minutes. Elisa as a provider of vital service failed to report the fault to RIA.
https://geenius.ee/uudis/elisa-vea-tottu-ei-saanud-paev-otsa-112-helistada-firma-jattis-sellest-teavitamata/
Tag Archives: Anto Veldre
TUT Cyber Conference 2018

Conference agenda:
10:00-10:30 Registration, cofee and cookies
10:30 Opening words by TUT rector Jaak Aaviksoo;
Kusti Salm, Ministry of Defense and Maarja Kirtsi, Estonian Internet Foundation
10:45-13:00 “Does Estonia needs cyberinsurance?”Moderator: Anto Veldre
10:45 Cybersecurity Challenges. Lauri Luht, RIA
11:15 In the feature everything will be better? or more horrible? Aare Reintam, NATO CCD COE
11:45 Kalev’s active and professional activities with technological means to preserve health
12:00 Is self-driving cars a real danger to society? Krister Kalda, TUT Mektory
12:20 Cybercrime does not cry on arrival! Karen K Burns, CGI
12:40 To buy cyber insurance or not? Helen Evert, IIZI Kindlustusmaakler AS13:00-14:00 Lunch
13:10-13:35 CyberSecurity TV-game show at American corner with Ralph Echemendia, Seguru and Marily Hendrikson, Startup Estonia (ENG)
13:40-13:55 MWB LAB Launch@TTÜMektory
14:00-15:10 Parallel sessions on various topics:
• Main hall: Human factors & OSINT by Jenny Radcliffe, Host of The Human Factor Podcast, UK & Lisa Forte, Red Goat Cyber Security, UK (Cyber Security SummerSchool) (ENG)
• How to build a cyber defense plan for your institution? Raido Orumets, BCS Training. Room: 108 Labor Market for Business Models.
• How to learn to think in the way rafter thinks and protect yourself from evil eyes? Peeter “Technocrat” Marvet, Zone Media resident hacker. Room 111 “Learning to Play”.
• Failure of one rafter due to the digital forensics, Toomas Lepik, TUT and How to hack contactless cards? Kadri Lenk, Eesti Energia and Raido Roben, Datanor. Room 125 Logistics.
• Ransomware simulation and MWB LAB launch@TTÜMektory, Malwarebytes (ENG). Room 109 and 209 – MWB Labs.15:10-15:20 Kalev Kahoot game (ENG) (please be ready! https://kahoot.it/)
15:20-16:00 Main hall: Panel Discussion on Maritime Cyber Security (ENG).
Moderator: Kieren Nicolas Lovell, University of Cambridge, UK. Panelists: Adrian ‘Tel’ Venables, Lancaster University; Jenny Radcliffe, Host of The Human Factor Podcast, UK; Jeff Moulton, Stephenson’s National Center for Security Research and Training and the Transformation Technologies and Cyber Research Center at Louisiana State University, USA; Marina Martinez (TBC), The Spanish Office for Science and Technology (SOST), Spain.16:00
• CyberSpike Competition Award Ceremony (EST / ENG)
• Cake
Links:
https://ttu.ee/ttu-korraldab-12-juunil-esimest-kuberkonverentsi-eestis
https://sites.google.com/view/kyberolympia/reeglid-2018/konverents-2018
Personnel changes in RIA cyber security division

Anto Veldre, a legendary Estonian security specialist leaves RIA:
From the beginning of the year, the State Information System Authority (RIA) discharged an experienced IT security expert and promoter Anto Veldre. Veldre has worked as an analyst at the incident handling department at CERT-EE and in the Communications Department.
Helen Uldrich, head of RIA Communications Department, explained the discharge of Anto Veldre by the change in the structure of their unit from 2018. The analyst’s place where Veldre previously worked was changed into a spokesperson’s position and, as a result, his duties changed.
“Unfortunately, RIA did not have another position to offer Anto that would correspond to his professional profile. The whole staff of the State Information System Agency highly appreciates Anto and his contribution, for example, to explaining the functioning of the e-state,” added Uldrich.

Klaid Mägi, the head of CERT-EE leaves RIA:
Klaid Mägi, head of CERT-EE will leave the state office and continue to work at CybExer Technologies, a private Estonian company promoting cyber hygiene. Mägi has led the unit since autumn 2014. Previously, he has worked at the Ministry of Finance, Elisa and Elion.

Uku Särekanno, the new Deputy Director General of RIA Cyber Security Branch:
The authority organised a public competition last October to find a director for the Cyber Security Branch. About ten people applied for the position. The Director General of the Information System Authority chose the suitable candidate in early December.
Previously, Uku Särekanno has worked at different positions in the European Commission, the Government Office, and the Ministry of Foreign Affairs, led the Public Order and Criminal Policy Department of the Ministry of the Interior, and represented Estonia in Brussels regarding issues of migration and police cooperation.
Before, since September 2011, this responsibility has been borne by Toomas Vaks, who previously worked as a risk manager for bank cards in Swedbank, before he was employed at Hansapank.
Links:
https://tehnika.postimees.ee/4367831/ria-koondas-legendaarse-eesti-turvaspetsialisti-anto-veldre
https://geenius.ee/uudis/ria-koondas-eesti-turvaspetsialisti-anto-veldre/
https://www.err.ee/654409/ria-uks-juhivtootaja-klaid-magi-lahkub-toole-erasektorisse
https://geenius.ee/uudis/riast-lahkus-toolt-jargmine-tippekspert-certi-juht-klaid-magi/
https://geenius.ee/uudis/peterkop-me-ei-suuda-erasektoriga-voistelda-aga-pakume-erilist-tood/
https://www.ria.ee/en/uku-sarekanno-is-the-deputy-director-general-of-the-information-system-authority.html
https://geenius.ee/uudis/uus-eesti-kuberkaitse-juht-meie-maine-hoidmiseks-ei-piisa-enam-ainult-raakimisest-ja-konverentsidel-kaimisest/
http://arileht.delfi.ee/news/uudised/ria-endine-kuberturbejuht-macgyveri-teibiga-e-riiki-ei-ehitata?id=79908056
SK Annual Conference 2017

E-identity event SK Annual Conference 2017 will take place on November 2, 2017, Baltic Station old waiting area (Toompuiestee 37, Tallinn).
Agenda:
09:00-09:30 Registration and morning coffee
09:30-10:30 Overview of SK 2017, Kalev Pihl, SK
10:30-11:00 Smart-ID: fast start and future plans, Kaido Irval and Georg Nikolajevski, SK
11:00-11:15 Cofee Break
11:15-11:45 The future of authentication in SEB. When will the code cards disappear? Ragnar Toomla, SEB
11:45-12:15 DeepScan, Lauri Ilison, Nortal
12:15-13:00 Lunch
13:00-14:00 Keynote: The Future of Technology Through the Mind of a Hacker, Pablos Holman
14:00-14:45 Panel discussion, Pablos Holman and Taavi Kotka
14:45-15:00 Cofee Break
15:00-15:30 RSA (implementations) attack history and lessons, Arne Ansper, Cybernetica
15:30-16:00 eID year in retrospect, Anto Veldre, RIA
16:10-16:40 Round of question and answers
16:40-17:00 Summary of the day by digital world enthusiasts
17:00-18:00 Evening snack
Registration till October 20.
Links:
https://www.sk.ee/ettevottest/sk-aastakonverents/aastakonverents-2017
ETV “Suud Puhtaks” debate on internet voting security

Is the cyber security in Estonia ensured? Why the government wants to change the period of i-voting and what signal with that we send to the world? Talk show host Urmas Vaino helps to set things straight.
Debating:
Indrek Saar, Minister of Culture, Social Democratic Party
Jaanus Karilaid, Member of Parliament, Center Party
Priidu Pärna, Member of Tallinn City Council, Pro Patria and Res Publica Union
Anto Veldre, RIA analytic
Kristjan Vassil, UT senior researcher
Märt Põder, organizer of journalism hackathon
Arti Zirk, TUT IT faculty student
Tarvi Martens, Electoral Committee, Head of Internet Voting
Kristen Michal, Member of Parliament, Reform Party
Mihkel Slovak, UT senior researcher
Henrik Roonemaa, Geenius.ee editor
Erki Savisaar, Member of Parliament, Center Party
Andres Kutt, RIA, IT architect
Sven Heiberg, Cybernetica AS, Project Manager of Internet Voting System
Jaak Madison, Member of Parliament, Conservative People’s Party
Jaanus Ojangu, Chairman of Free Party
Agu Kivimägi, Stallion cyber security consultant
Jaan Priisalu, TUT researcher
Silver Meikar, Adviser to Minister of Culture
Kalev Pihl, SK ID Solutions, Board Member
Oskar Gross, Head of Cyber Crime Unit of Central Criminal Police
Klaid Mägi, RIA, Head of the department for handling incidents (CERT-EE)
Heiki Kübbar, Founder of ICEfire OÜ
Birgy Lorenz, Board Member of Network of Estonian Teachers of Informatics and Computer Science
Andres Kahar, KAPO Bureau Manager
Sven Sakkov, Director of NATO Cooperative Cyber Defence Centre
Heiki Pikker, TUT Cyber Security MSc student
Links:
http://www.err.ee/587007/suud-puhtaks-kui-turvalised-on-e-valimised
http://etv.err.ee/v/paevakajasaated/suud_puhtaks/saated/8d5babc5-cc33-4ed5-9bc0-927d4293ee21/suud-puhtaks
http://news.err.ee/310788/center-party-wants-to-shorten-e-voting-period
Study on the lifecycle of cryptographic algorithms 2016

This study is a natural continuation of three previous studies conducted in 2011, 2013 and 2015. The fourth version of cryptographic algorithms life cycle study published on June 9, has more than 10 authors and has 163 reference source. The 2016 report is the first one in its sequence to be written in English, because the study is unique on a global scale, and the previous versions has been of great international interest.
The foreword of the report has been written by Anto Veldre:
The Dutch DigiNotar case in 2011 demonstrated the hard choices a country faces if a PKI supporting its government’s IT systems is compromised. [..] Therefore, it was decided in 2011 to assemble a scientific task force to analyse the problems and risks that reliance on cryptography is posing on the sustainable functioning of our society.
Among the usual topics in cryptography, there is quite revealing section “Cryptographic protocols over radio connection”. For example, there the authors find that Estonian public transportation cards are vulnerable to various kinds of Denial of Service and cloning attacks:
The transportation cards in Tallinn are built on MIFARE Classic, whereas in Tartu MIFARE Ultralight C cards are used. However, even though both of the cards support cryptographic authentication, this functionality is not used. In both cases, the protocol running between the card and the reader is essentially the same, consisting of transmitting the card’s unique ID and a signature. [..] While this measure prevents unauthorised parties from issuing new cards, it does not stop the card cloning attack. [..] Cloning a card that carries a monthly ticket causes direct financial loss to the transportation service provider and must hence be urgently addressed.
Even though the ID fields of transportation cards are not writeable, other fields may be. This is for example the case with Tartu bus cards that allow e.g. the signature field to be overwritten by a standard app working on a regular NFC-capable smartphone. As a result, the card will become invalid, giving us a potential Denial of Service attack.
The report analyzes different radio frequency card technologies used for physical access control. There are many problems – transparency issues, use of weak cryptography or no cryptography at all. The authors have also interviewed Hardmeier and G4S to study deployment issues. Some of the deployment issues revealed are quite disturbing:
Interview with a company installing NFC-based access control systems revealed that it is common practice to use same keys also in several installations, making e.g. door keys of one company work at the door of another company, too.
Links:
https://www.ria.ee/public/RIA/Cryptographic_Algorithms_Lifecycle_Report_2016.pdf
https://www.ria.ee/ee/eriik-2018-valmis-2016-aasta-kruptograafiliste-algoritmide-elutsukli-uuring.html
https://blog.ria.ee/ria-aastakonverentsi-i-sessiooni-otseblogi/
SK Annual Conference 2015

E-identity event SK Annual Conference 2015 will take place on November 5, 2015, Vabal Laval Telliskivi Loomelinnakus (Telliskivi 60a, C1-hoone)
09:00-09:30 Registration and morning coffee
09:30-09:45 Overview of SK 2015, Kalev Pihl, SK
09:45-10:45 Identification physically and digitally, Joseph Leibenguth, Gemalto
10:45-11:15 Coffee Break
11:15-11:55 eIDAS and international interoperability, Katrin Laas-Mikko, SK
11:55-12:25 New Mobile-ID and alternatives, Urmo Keskel, SK
12:25-12:45 NutiKaitse 2017: development of security, Andri Möll, Monday Calendar
12:45-13:30 Lunch
13:30-14:00 Life of cryptography, Anto Veldre, RIA
14:00-14:30 Underlying technologies of cryptocurrency, Asse Sauga, Eesti Krüptoraha Liit
14:30-15:40 Tech trends 2030 & company of the future, Richard van Hooijdonk
15:40-16:00 Coffee Break
16:00-16:35 Questions and answers
16:35-16:55 Summary of the day
16:55-17:30 Evening snack
Hundred thousand ID card certificates issued with invalid public key encoding
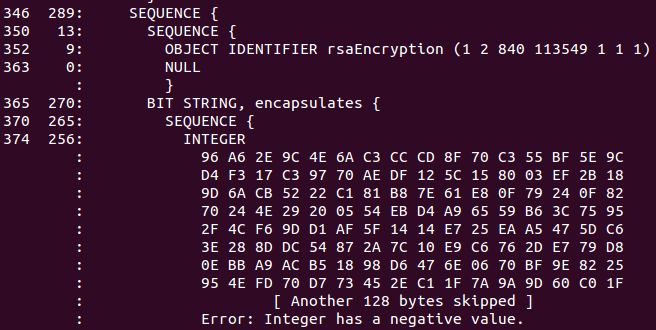
From the Chrome bug report:
Estonian IDs issued between September 2014 to September 2015 are broken and use negative moduli.
Not content with signing negative RSA moduli, still other Estonian IDs have too many leading zeros.
In Estonia there are 100 000+ such ID-cards and without any change with chrome 46 those card owners could not use chrome any more for every day usage.
ASN.1 DER encoding specifies that positive integer [having msb of MSB set] has to be encoded with 0-byte prefix. However, the certificates in question omit 0-byte prefix for RSA public key modulus and therefore standards complying Chrome DER decoder interprets public key value as an [invalid] negative integer.
Google developer hints that SK’s recently passed annual audit falsely attests that SK operations confirm to the standards:
It would seem each of these certificates fails to conform to the ETSI TS 102 042 policies (for which sk.ee was audited), which would invalidate them for use as QCP-SSD/QCP/NCP, nor would they conform to the sk.ee CPS in force at this time. If so, wouldn’t all of these certificates need to be revoked, per sk.ee’s CPS?
First SK asked for a “temporary” workaround, later committing to recall the ID cards in question in the next 6 months:
Is there possible to make temporary (for 5 years) workaround for such cards in chrome 46 and beyond?
AFAIK, no more certificates with incorrect encoding are being generated and the renewal of the issued ones is being planned. It shall require time, less than 5 years but obviously not a month or two, due to the sheer number of the cards out there.
6 months seems like a realistic target.
Translation of Postimees article:
Due to a software failure by Estonian ID card software vendor AS Sertifitseerimiskeskus about 250 000 ID cards have an error that may in the future cause its usage problem. ID cards with software faulty certificates were issued for one year since September 2014 and if error is not fixed in the following six month, then people will not be able to authenticate themselves anymore in the future versions of the world’s second most popular web browser Google Chrome.
“This is certainly non-compliance with standards on our side. We let error through in our software development. Reason, why this error went through and was permanent is that no browser had discovered it until now and our ID card so far works with them excellent” head of SK Kalev Pihl explains to Postimees. The thing come to light when Google made a big software update which controls subtlety, what no other software have done so far. “It came out that some certificates on Estonian ID cards do not conform to requirements,” says Kalev Pihl, who says that the error came out during the beta-testing of the new browser software.
Pihl confirms that SK agreed with Google for a half year long transition period. Result is that Chrome will not add the new software at the moment and people can use this browser for authentication with no problem. “That half a year of development time should be really enough in order to provide to a person a solution where he/she can renew ID card certificates behind the computer with one button press,” adds Pihl. “Usually during our testing we discover bugs introduced by browser developers, this time they discovered error on our side,” summarized Pihl.
RIA plans a remote update feature for Estonian ID cards / e-residency cards:
The functionality, prompting card owners to update the certificates online, has once been part of the Estonian ID card software suite and will now be re-implemented. The procedure of initiating the remote update procedure on the certificates is to be implemented in a way that is both easy to use and secure. Veinthal said the security and risk of the new functionality were to be analysed before implementation. “The eID framework has to be aware that interoperation glitches are becoming more frequent in the world of technology, increasing the necessity to create fast and convenient solutions,” commented Veinthal.
Links:
https://code.google.com/p/chromium/issues/detail?id=532048
https://code.google.com/p/chromium/issues/detail?id=534766
http://tehnika.postimees.ee/3342861/eestis-on-kaibel-sadu-tuhandeid-tarkvaraveaga-id-kaarte
http://news.err.ee/v/scitech/d95562b3-2d28-4d1c-bfce-487a6420caa5/250000-estonian-id-cards-could-be-faulty
https://blog.ria.ee/probleem-nr-532048/
http://news.postimees.ee/3348383/all-e-residents-got-faulty-cards
https://www.ria.ee/ria-plans-a-remote-update-for-estonian-id-cards/
http://news.err.ee/v/scitech/e6f4c240-b0f4-4543-a9fe-fa83a2101f10/id-card-bug-could-damage-estonias-it-image
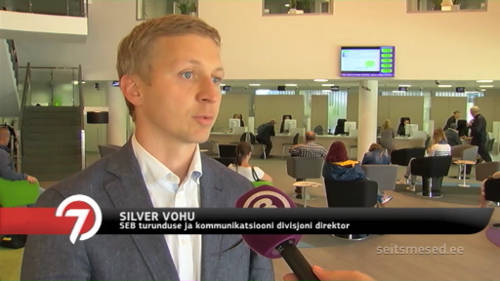
SEB Estonia Internet bank ID card authentication bypass
The flaw in SEB Estonia Internet bank allows to login just by knowing the victim’s username. The consequences of the flaw go beyond the read-only access to victim’s transaction history. The victim can be impersonated in any website that supports authentication through SEB (eesti.ee, mnt.ee, tele2.ee, etc.). The flaw can be abused to buy goods from online merchants (as shown in the video) since SEB does not require signature authorization for “banklink” transactions.
Timeline:
2015.05.11. 13:00 – reported to CERT-EE
2015.05.14. 12:00 – fixed by SEB Estonia
The time that was required for SEB to fix such a critical flaw surprises a bit.
SEB’s response:
SEB spokesman commented that “referred security issue existed in so-called laboratory conditions meaning that it needed several conditions to coincide and a specific knowledge”.
“Security issue got fixed and we also checked that the flaw was not maliciously exploited” said SEB’s spokesman and added that the problem got fixed faster than in an hour, after all the needed information was received.
Anto Veldre (RIA): It is better that ethical people with academic degree are looking for security holes than cyber criminals doing it. People should understand that new technology is complicated, systems at home and servers need to have updates everyday there is no such a thing like secure system (security) but there are people and control methods, if there is a problem it will be handled and afterwards logs are checked if something really happened.
Silver Vohu (SEB): It took less than an hour to make a fix. But reproducing the situation took most of the days and asking additional questions from CERT-EE was needed. In normal situation it was impossible to reproduce the problem.
Links:
https://www.youtube.com/watch?v=rRB8jZnS5nY
http://forte.delfi.ee/news/tarkvara/tosine-turvaauk-seb-internetipanka-sai-sisse-ainuuksi-kasutajanimega?id=72291205
http://tehnika.postimees.ee/3306453/seb-internetipangas-oli-tosine-turvaauk-sisenemiseks-piisas-vaid-kasutajanimest
http://seitsmesed.ee/eesti/uudis/2015/08/26/tosine-turvaauk-seb-internetipanka-sai-sisse-vaid-kasutajanimega/
http://www.tv3play.ee/sisu/seitsmesed-uudised-2015/648229
Concerns about European Commission’s plans to backdoor Estonian ID card

The European Commission presented a new plan for internal security, which is driven by the concern that powerful encryption is helpful to crime and terrorism. The initiative will not leave Estonia untouched as currently ID card provides encrypted communication ability.
Prime Minister Taavi Rõivas announced that Estonia should not give up to pressure by allowing to create a backdoor in ID card. Taavi Rõivas confirmed to Eesti Päevaleht and Delfi that cybersecurity and data confidentiality is fundamentally important.
He added that the law enforcement authority will have to find other ways to control crime, “Estonia is of the view that the fight against crime will have to find other means and not at the expense of ID card security“.
While the ID card software package includes utility that can be used to encrypt files, average Estonian does not use ID card to encrypt his communications, but merely use it as an authentication tool. Unless this significantly changes, the encryption ability provided by ID card will not be of significant interest to law enforcement authorities.
Even today, If a law enforcement authority would want to decrypt files encrypted with ID card, they could use official feature built into the ID card which lets ID card manufacturer to reset PIN code and gain authorization to private key operations (i.e., decryption).

Anto Veldre: This it is not very likely that some criminal would like to go to migration authority, give biometrics to the government and start to encrypt. Isn’t there any easier way to do it? Western world do not like that terrorist can send encrypted emails.
Interviewer: Is Estonian ID card in danger on the background of Europol requirements/thoughts?
Anto Veldre: I don’t think so. Estonian representatives in EU can handle this problem on political level (show the danger and peoples’ trust in current system). Police have their own techniques and they can handle their work.
Links:
http://epl.delfi.ee/news/eesti/politseile-oigus-id-kaardi-koodi-murda-euroopas-tahetakse-krupteerimisele-ametlikke-tagauksi?id=71438223
http://epl.delfi.ee/news/eesti/roivas-id-kaarti-kompromiteerida-ei-tohi-kuritegevusega-voitlemiseks-tuleb-leida-teised-viisid?id=71443761
http://etv.err.ee/v/meelelahutus/terevisioon/saated/4d030bd7-c496-476c-9f21-551007d89c06 (39:32 – 46:43)
http://uus.minut.ee/tagauksed-kruptos-ja-id-kaart/