Interesting quotes from the report:
In 2014, RIA aggregated its functions related to guaranteeing cyber security in the cyber security branch. Incident response, risk control and regulation supervision, as well as research and development activities are now determined more clearly, which also allows for a more efficient use of resources.
Skilful phishing of cloud service accounts (e.g. Gmail, Hotmail), which has continued at unprecedented levels at the beginning of 2015 as well. E-mails seem to be coming from a seemingly trustworthy source and have significantly improved in quality both content and Estonian language wise, which means that the receiver of the e-mail has to be even more attentive and critical in order to detect the fraud.
Intrusion into websites is more difficult to identify. It is becoming more common that the infector uploads the malware for a very short time period and takes into consideration, which IP-address is used to visit the site. For instance, if users visit the website from Estonia, they receive a different type of malware than the users who access the website from the USA.
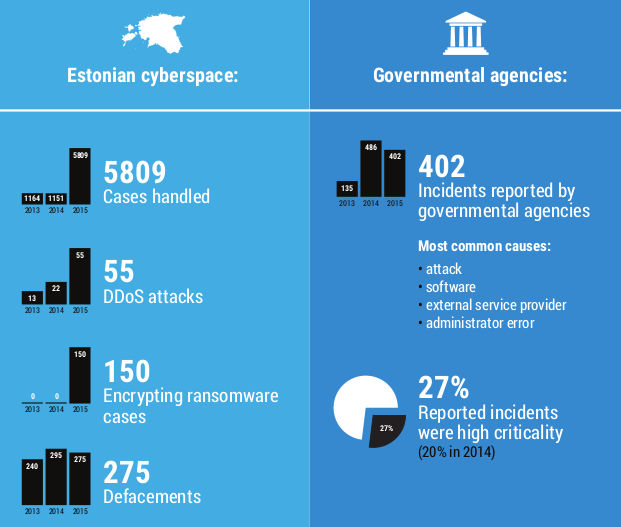
In 2014, there was a slight increase in the percentage of incidents that had actual consequences for the institutions and users. For instance, the use of document management system was disabled or, in more severe cases, digital prescription or Schengen information systems were down.
The incidents at the end of the year were mainly virus outbreaks and well-aimed phishing letters, but also distributed denial of service attacks, many of which did not last for a very long time, but according to RIA’s estimate, seemed to be mapping the resilience of systems.
As the life cycle of all algorithms is limited, the time to act in order to update all the cryptographic methods of services is even more limited. At some point, it might appear that smooth transition period has not been sufficient; e.g., when powerful quantum computers are used to break the cryptography. We need to have an action plan for the scenario when any of the algorithms important for some Estonian e-service has been broken. RIA sees a clear need to have such plans and to rehearse them.
The results of the Eurobarometer 2014 survey showed that Estonians trust the state as the guard of personal data more than in Europe on the average. Estonians are also less worried about the consequences of cyber-attacks and claim to be good at identifying fake e-mails.
On 1 July 2014, the Act for the Amendment and Application of the Law Enforcement Act entered into force. Pursuant to this act, starting from summer 2014, RIA is a law enforcement body. According to the changes, the Technical Regulatory Authority’s supervisory competency of guaranteeing the security and integrity of communication networks and services set in the Electronic Communications Act was transferred to RIA. The same draft also established RIA’s supervisory competency in the Emergency Act and the Public Information Act.
On 11 September, the government approved the “Cyber Security Strategy for 2014–2017” and its implementation plan. The strategy continues to target several goals set in the previous cyber security strategy, but there have also been new risks and requirements added. The dependency of the functioning of the state on information technology has increased and cross-dependencies have also increased, meaning that the provision of several critical services is no longer dependent on the functioning of Estonian IT-systems but also on the infrastructure and e-services in other countries.
In 2014, RIA, in cooperation with its partner organisations, developed common principles of readiness for emergency and cooperation in case of large-scale cyber incidents. An interagency working group lead by RIA prepared the draft for the Government of the Republic’s order “Plan for solving a large-scale cyber incident emergency”.
In addition to reacting to everyday vulnerabilities and risks, the key words for RIA in 2015 are improving the monitoring and resilience of the government network, cooperation with the field of medicine and solutions and risks related to the e-residents programme.
Links:
https://www.ria.ee/public/Kuberturvalisus/RIA-Kyberturbe-aruanne-2014_ENG.pdf
http://news.err.ee/v/scitech/1c0f2c7b-8f3d-49cf-9cf3-c04b4f0a4171