July 10-14, 2017, Estonian Information Technology College, Tallinn
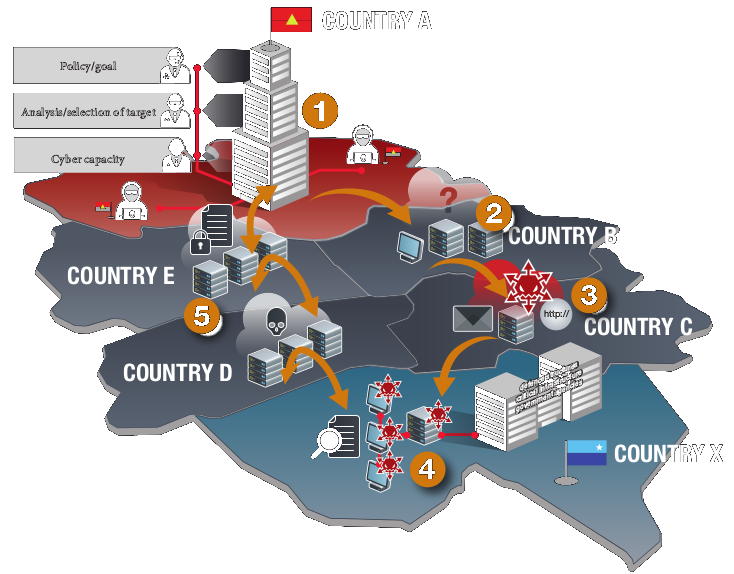
A main focus on this year’s Cyber Security Summer School will be social engineering. With experts from all faculties, including computer science, law, criminology, forensics and psychology, the Summer School tries to give an impression on how and why social engineering works, how to prevent social engineering and how to find evidence for social engineering attacks.
Speakers:
Dirk Labudde, The University of Applied Sciences Mittweida, Germany
Jeffrey Moulton, Louisiana State University, USA
Sandra Matz, University of Cambridge Psychometrics Centre, UK
Vesselin Popov, University of Cambridge Psychometrics Centre, UK
Monday, July 10th
08:00 – 09:00 Registration. Breakfast at IT College bitStop Cafe
09:00 – 09:30 Welcome by the organizers. Practical information
09:30 – 10:30 Introduction of the speakers and mentors. Allocation of teams
10:30 – 11:00 Coffee break
11:00 – 12:30 Talk by Freddy Dezeure “Main Cyber Threats Affecting Our Society and How Your Social Footprint Helps the Adversary”
12:30 – 13:30 Lunch break at IT College bitStop Cafe
13:30 – 14:30 Talk by Aunshul Rege “Tainted Love: Social Engineering at Dating Websites”
14:30 – 15:30 Cases by Kieren Niĉolas Lovell
15:30 – 16:00 Coffee break
16:00 – 17:00 Introduction to CTF. Introduction of CTF-teams
17:30 – 20:00 Dinner and welcome party at IT College bitStop Cafe
Tuesday, July 11th
08:00 – 09:00 Breakfast at IT College bitStop Cafe
09:00 – 10:00 CTF-team-time
10:00 – 11:00 Talk by Didier Meuwly
11:00 – 11:30 Coffee break
11:30 – 12:30 Talk by Vesselin Popov on Big Data, Psychometrics and Profiling
12:30 – 13:30 Lunch break at IT College bitStop Cafe
13:30 – 14:30 Social Engineering Talk by Dirk Labudde
14:30 – 15:00 CTF-team-time
15:00 – 15:30 Coffee break
15:30 – 16:15 Talk by Tobias Eggendorfer: How (not) to be phished
16:15 – 17:00 CTF-team-time
17:30 – 18:30 Dinner at IT College bitStop Cafe
Wednesday, July 12th
08:00 – 09:00 Breakfast at IT College bitStop Cafe
09:00 – 09:30 Presentations by CTF-teams on their results
09:30 – 10:30 Hands on Session by Dirk Labudde (Part 1)
10:30 – 11:00 Coffee break
11:00 – 12:30 Hands on Session by Dirk Labudde (Part 2)
12:30 – 13:30 Lunch break at IT College bitSop Cafe
13:30 – 15:00 Talk by Ralph Echemendia
15:00 – 15:30 Coffee break
15:30 – 16:15 Talk by Aleks Koha and Leonardo Romanello on Tools against Social Engineering
16:15 – 17:30 Briefing on the morning presentation, status update on the flags and CTF-team-time
17:30 – 18:30 Dinner at IT College bitStop Cafe
Thursday, July 13th
08:00 – 09:00 Breakfast at IT College bitStop Cafe
09:00 – 10:30 CTF-team-time
10:30 – 11:00 Coffee break
11:00 – 12:30 CTF-team-time
12:30 – 13:30 Lunch break at IT College bitStop Cafe
13:30 – 15:00 Talk by Jeffrey Moulton “Privacy in the Digital World”, “This is Personal – Part II, The Internet of You”
15:00 – 15:30 Coffee break
15:30 – 17:30 CTF-team-time
18:30 Bus transfer IT College – city centre
19:00 – 22:00 Reception dinner in the Crown Hall of the Tallinn Teachers’ House (Tallinna Õpetajate Maja) at the Town Hall Square (Raekoja plats 14).
22:30 Bus transfer city centre – IT College
Friday, July 14th
08:00 – 09:00 Breakfast at IT College bitStop Cafe
09:00 – 09:30 Status of CTF-Teams
09:30 – 10:00 Last flags for CTF
10:00 – 12:30 Presentations by CTF-Teams on their results
12:30 – 13:30 Lunch break at IT College bitStop Cafe
13:30 – 15:00 Report writing and feedback
15:00 – 15:30 Coffee break
15:30 – 16:30 Announcing the winner of CTF. Wrap-up, defusing, feedback to the organizers
16:30 – 17:30 Dinner at IT College bitStop Cafe