Peeter Marvet dispels the myth of transparency in finding out who has accessed your data in state databases:
For the past 20 years or so Estonian e-government and the X-Road backbone has been promoted with the promise of transparency. Yes, we keep a lot of data, but it is stored securely and you can always check who has accessed it. This means transparency and trust. Or “trust”, as in this The Guardian interview with Toomas Henrik Ilves.
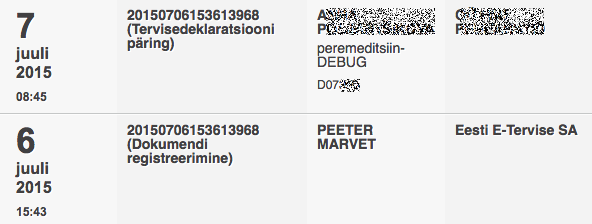
Problem is, there is no such transparency – no notifications, no place to log in and see who has accessed your data. There was one system with such functionality, but it was shut down like 10 years ago (added: there is one system – E-Health’s Digilugu.ee “patient portal”). And even when it worked, it displayed only trivial amount of accesses [..].
The rest of the databases? I recall a meeting (in the government residence, no less) where the topic was discussed, possibly on a roundtable arranged by the National Audit Office. After some serious googling I found a contact address where to submit a request to get information about who has accessed my data in the Population Registry. It took some months to get the answer, it supposedly had information about who had requested my data available only in the “comments field” and had to be assembled manually. Promoting the idea to requesting such transparency is a good start for denial-of-service attack on Estonian e-government.
Then there was a case when somebody from the Ministry of the Interior was to promote some new legislation mandating more data storage with the argument, that everybody is able to see who has been accessing the data, so it is not a privacy violation. Our correspondence with her ended after couple of rounds, after she was unable to find any proof of solution where I could view the access log.
And don’t get me started on the question of who can purchase the data from our Population Registry or from Business Register. Want to get contacts of unemployed pensioners? Give us your monies! Want to spam every e-resident who has created a company? Sure, all addresses in registry must be business contacts so spam away (and give us some monies)!
Interesting research to conduct would be to submit bunch of requests for personal data access reports to various state database holders and analyze the response time and the detailedness level of the answers.
Links:
https://tehnokratt.net/2016/05/meme-based-trust-lockean-contract-la-e-stonia/









