
Videos, proceedings and other materials from the 7th Conference on Cyber Conflict, CyCon 2015, are now available online.
Links:
https://ccdcoe.org/cycon/2015/
https://ccdcoe.org/cycon-2015-materials-now-public.html

Videos, proceedings and other materials from the 7th Conference on Cyber Conflict, CyCon 2015, are now available online.
Links:
https://ccdcoe.org/cycon/2015/
https://ccdcoe.org/cycon-2015-materials-now-public.html

An unique device was noticed on the table of Tallinn deputy mayor Kalle Klandorf during a interview which took place on Thursday. It is probably a jammer. Jammer is an electronic device which fills specific frequencies with electromagnetic noise. Other devices using the same frequencies are unable to transmit.
Even though the exact inscription is not seen, it may be [this device, costing USD 208]. The device blocks frequencies 925-960 MHz, 1805-1880 MHz and 1930-1990 Mhz used for mobile phones. It also blocks WiFi connection on 2.4GHz and UHF frequencies 400-470 MHz.
Klandorf laughed at the question if there is an jammer on his table. “I haven’t noticed. Maybe it’s not mine? I haven’t bough. I don’t know” he replied. He suggested that it may be a handheld radio. Ten of those were recently bought for the municipal police and crisis team. Klandorf thought that it could be a amplifier. Considering wiretapping, Klandorf said that he wouldn’t mind if they listen.
According to Electronic Communication Act p. 23 it is forbidden to use devices which create interference and disturbs radio communication. It is forbidden to sell, facilitate etc. and importing into EU. [According to the Technical Regulatory Authority], it is forbidden to allow such devices to the market and take into use because they do not comply with the regulations.
The use of frequency jammers is probably one of the methods how bribery allegations facing mayor of Tallinn tried to prevent eavesdropping by KAPO.
Comment by Estonian jammer vendor:
According to research director of OÜ Rantelon professor emeritus Andres Taklaja, the device in Klandorf’s office is meant to interrupt wiretapping devices. OÜ Rantelon produces commercial jamming devices for govermental agencies and defence forces. He said that most certainly it is a jammer. It looks like a cheap jammer with separate antenna for every frequency range. He suggested that if there is a jammer, then there must be bugs.
“These gentlemen should know the frequencies used by the bugs as they were former militiamen. They probably chose the device according to the potential bugs. The looks of the device depends on the frequencies it is meant to interfere. The length of the antennas depends on the wavelength of the radio-waves. It is possible to deduce the frequencies by external observation.”
“If the device is too powerful, then it may interfere with other equipment in the building, so I suspect that it is quite low-power. The device is powered from the plug and the power can be adjusted. It could have a battery but such devices take quite a lot of power. If it is unplugged, then it is probably turned off.” Rantelon produces bigger and more powerful devices as they are meant to be used in the field. The professor didn’t suggest how the deputy mayor could have obtained the jammer.

October 29, 2015. Estonian National Library, Tallinn.
Agenda
09:30 – 10:00 Registration open, welcome coffee.
10:00 – 10:10 Opening remarks
Andrus Padar, Chief of Cyber Defense League
10:10 – 11:30 Is Estonian e-lifestyle well defended?
– short presentations and demos by cyber league members.
11:30 – 11:45 Coffee pause
11:45 – 13:00 Cyberwar and cybercivilwar – patriot or cyberterrorist?
attorney at law Eeva Mägi, Maria Mägi Law Firm, doctoral student at Tallinn University of Technology
13:00 – 14:00 Lunch
14:00 – 15:30 Cyberdefender or cybercriminal – where is the dividing line between allowed and forbidden?
attorney at law Mare Tannberg, Maria Mägi Law Firm, University of Tartu lecturer in criminal law.
15:30 – 15:45 Coffee pause
15:45 – 17:00 Roundtable, moderator Andrus Padar and Maria Mägi (Maria Mägi Law Firm Managing partner).
Working language Estonian. Participation fee EUR 25. Invitation only event. Ask invitation from your closest Cyber Defense League member.
Links:
https://kkl.conf.ee/doku.php
From the Chrome bug report:
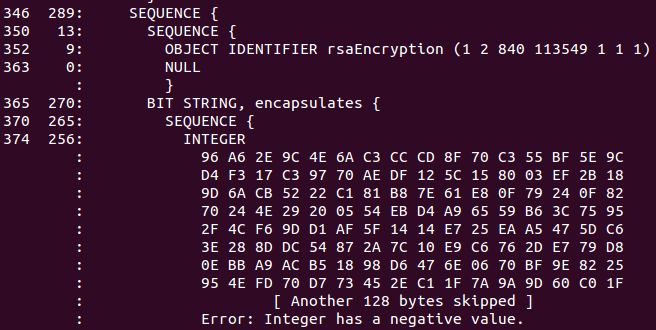
Estonian IDs issued between September 2014 to September 2015 are broken and use negative moduli.
Not content with signing negative RSA moduli, still other Estonian IDs have too many leading zeros.
In Estonia there are 100 000+ such ID-cards and without any change with chrome 46 those card owners could not use chrome any more for every day usage.
ASN.1 DER encoding specifies that positive integer [having msb of MSB set] has to be encoded with 0-byte prefix. However, the certificates in question omit 0-byte prefix for RSA public key modulus and therefore standards complying Chrome DER decoder interprets public key value as an [invalid] negative integer.
Google developer hints that SK’s recently passed annual audit falsely attests that SK operations confirm to the standards:
It would seem each of these certificates fails to conform to the ETSI TS 102 042 policies (for which sk.ee was audited), which would invalidate them for use as QCP-SSD/QCP/NCP, nor would they conform to the sk.ee CPS in force at this time. If so, wouldn’t all of these certificates need to be revoked, per sk.ee’s CPS?
First SK asked for a “temporary” workaround, later committing to recall the ID cards in question in the next 6 months:
Is there possible to make temporary (for 5 years) workaround for such cards in chrome 46 and beyond?
AFAIK, no more certificates with incorrect encoding are being generated and the renewal of the issued ones is being planned. It shall require time, less than 5 years but obviously not a month or two, due to the sheer number of the cards out there.
6 months seems like a realistic target.
Translation of Postimees article:
Due to a software failure by Estonian ID card software vendor AS Sertifitseerimiskeskus about 250 000 ID cards have an error that may in the future cause its usage problem. ID cards with software faulty certificates were issued for one year since September 2014 and if error is not fixed in the following six month, then people will not be able to authenticate themselves anymore in the future versions of the world’s second most popular web browser Google Chrome.
“This is certainly non-compliance with standards on our side. We let error through in our software development. Reason, why this error went through and was permanent is that no browser had discovered it until now and our ID card so far works with them excellent” head of SK Kalev Pihl explains to Postimees. The thing come to light when Google made a big software update which controls subtlety, what no other software have done so far. “It came out that some certificates on Estonian ID cards do not conform to requirements,” says Kalev Pihl, who says that the error came out during the beta-testing of the new browser software.
Pihl confirms that SK agreed with Google for a half year long transition period. Result is that Chrome will not add the new software at the moment and people can use this browser for authentication with no problem. “That half a year of development time should be really enough in order to provide to a person a solution where he/she can renew ID card certificates behind the computer with one button press,” adds Pihl. “Usually during our testing we discover bugs introduced by browser developers, this time they discovered error on our side,” summarized Pihl.
RIA plans a remote update feature for Estonian ID cards / e-residency cards:
The functionality, prompting card owners to update the certificates online, has once been part of the Estonian ID card software suite and will now be re-implemented. The procedure of initiating the remote update procedure on the certificates is to be implemented in a way that is both easy to use and secure. Veinthal said the security and risk of the new functionality were to be analysed before implementation. “The eID framework has to be aware that interoperation glitches are becoming more frequent in the world of technology, increasing the necessity to create fast and convenient solutions,” commented Veinthal.
Links:
https://code.google.com/p/chromium/issues/detail?id=532048
https://code.google.com/p/chromium/issues/detail?id=534766
http://tehnika.postimees.ee/3342861/eestis-on-kaibel-sadu-tuhandeid-tarkvaraveaga-id-kaarte
http://news.err.ee/v/scitech/d95562b3-2d28-4d1c-bfce-487a6420caa5/250000-estonian-id-cards-could-be-faulty
https://blog.ria.ee/probleem-nr-532048/
http://news.postimees.ee/3348383/all-e-residents-got-faulty-cards
https://www.ria.ee/ria-plans-a-remote-update-for-estonian-id-cards/
http://news.err.ee/v/scitech/e6f4c240-b0f4-4543-a9fe-fa83a2101f10/id-card-bug-could-damage-estonias-it-image

All it took to trigger the widespread woe was an outwardly insignificant slip: on September 17th, Nets Estonia coordinating card transactions in Estonia forwarded a file with cards transactions to the financial institutions twice, and two days later attempted to correct the mistake by sending a file cancelling the «double» transactions.
The banks which for whatever reason only acted on the cancel-entries sent on September 19th, yesterday morning unexpectedly returned to customers the money spent on September 17th. This, for instance, was the lot of SEB clients. To our knowledge, clients of institutions like Swedbank and Citadele were less lucky. The control systems of said banks had already acted on the double file dating September 17th and brazenly pocketed the customers’ money twice.
As LHV and Nordea banks control systems pulled brakes both on the file prescribing double payments and dataset sent to cancel it, the clients of both escaped the mess.
Why LHV and Nordea engineers could implement fault tolerant algorithm while engineers of the two biggest banks SEB and Swedbank could not?
Links:
http://news.postimees.ee/3339225/confused-banks-erraneously-move-money-of-hundreds-of-thousands

By eavesdropping on telephone calls, the investigators were aware who and when Mr Savisaar met and what to keep in mind while collecting evidence. The investigators were aware that dark matters are not discussed over the phone, and that plain speech would be avoided if at all possible.
Here is where hidden cameras are helpful, installed by court permission. However, even these are in danger to be discovered. Especially with Mr Savisaar, as the all-suspecting Mayor of Tallinn is in the habit of asking people close to him «bug control» places linked to him from time to time. Therefore, Kapo was at pains to diligently plan where and for how long to install stuff.
Links:
http://news.postimees.ee/3337697/the-scandal-long-feared-laid-bare

On 13 October 2015 at 12.00pm, Mikko Hyppönen, the world renowned information security expert, whose presentations always contain ample examples of topical information security incidents and events that have endangered the privacy of Internet users will be delivering a public lecture at the IT College.
Links:
http://www.itcollege.ee/en/blog/2015/09/15/mikko-hypponen-top-specialist-of-information-security-will-be-delivering-a-public-lecture-at-the-it-college/
https://www.youtube.com/watch?v=UXSAaVx2EOo
http://uudised.err.ee/v/eesti/724d4692-24ba-48ee-ab60-b81221fbc79b/
http://news.err.ee/v/scitech/8067fe55-f06f-47be-aefa-38a2a1b834e2/

Upon manufacturing the ID card, residence card, Mobile-ID and Digi-ID certificate, email address in the form of name.surname@eesti.ee will be generated. In the case of namesakes, the software compares the email address to the previously used addresses and next people with the same name will get an email address in the following form: name.surname.1@eesti.ee, name.surname.2@eesti.ee etc., depending on how many people there are with the same name.
“Due to the software error, duplicate email addresses were created for namesakes, these addresses were also inserted to the certificates of identity documents. We have fixed the error and we can assure that such a situation will not reoccur in the future,” explained Kalev Pihl, the Member of the Board of the Certification Centre. Altogether 40 000 ID and residence cards were issued in June and July, 4120 of them were with duplicate email addresses.
Email address name.surname@eesti.ee is an alias to personalidentificationcode@eesti.ee, which is unique. For sending information, state authorities use the email address personalidentificationcode@eesti.ee.
After the software error was detected, the State Portal suspended the email forwarding right of all of these persons, who had received a duplicate email address with their certificates. These persons can start using their eesti.ee email address only after the renewal of the certificates.
Links:
https://www.politsei.ee/en/uudised/uudis.dot?id=471347