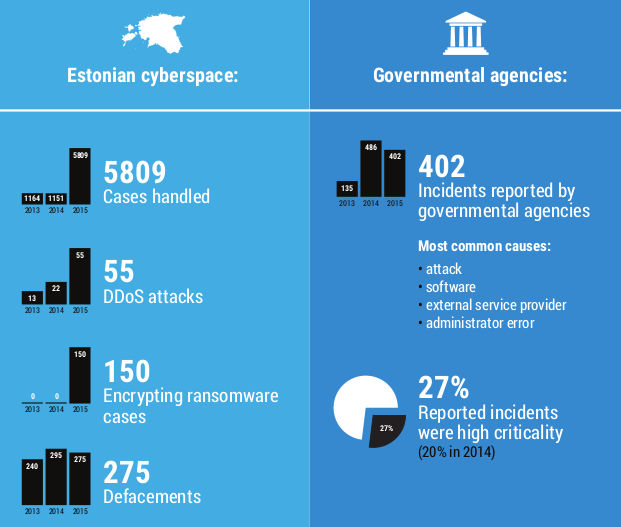
Defense committee: Dominique Unruh (chairman), Siim Karus, Vitaly Skachek, Dirk Oliver Theis, Raimundas Matulevicius.
A Cost-Effective Approach to Key Management in Online Voting Scenarios
Abstract: Since smart cards both offer reasonable prices and expose an API for development, this document evaluates different approaches to implement threshold encryption over smart cards to support an electoral process.
Student: Sergio Andrés Figueroa Santos
Curriculum: NordSecMob (MSc)
Supervisor: Sven Heiberg, Helger Lipmaa, Tuomas Aura
Reviewer: Ivo Kubjas
Defense: 02.06.2016, 09:00, Liivi 2-405Revision of Security Risk-oriented Patterns for Distributed Systems
Abstract: In this thesis, we target the secure system development problem by suggesting application of security risk-oriented patterns. The applicability of these security risk-oriented patterns is validated on business processes from aviation turnaround system.
Student: Silver Samarütel
Curriculum: Software Engineering (MSc)
Supervisor: Raimundas Matulevicius
Reviewer: Alexander Horst Norta
Defense: 02.06.2016, 09:00, Liivi 2-405Role Based Access Control as SecureUML Model in Web Applications Development with Spring Security
Abstract: In order to support and simplify the model-driven approach for a web application development with Spring platform, realization of a concept plugin for Eclipse IDE is proposed. This plugin supports the recognition of Spring Security notations with capability to visualize the RBAC model on top of them.
Student: Andrey Sergeev
Curriculum: Cyber Security (MSc)
Supervisor: Raimundas Matulevicius
Reviewer: Henri Lakk
Defense: 02.06.2016, 09:00, Liivi 2-405Secure and Efficient Mix-Nets
Abstract: This thesis studies a zero-knowledge shuffle argument proposed by J. Furukawa in 2005. Firstly, we provide a more detailed and easily readable description of the shuffle and shuffle-decryption zero-knowledge protocols than in the original paper. Secondly, we provide two new characterizations of a permutation matrix and two simple modifications of the shuffle protocol that reduce the computational complexity.
Student: Janno Siim
Curriculum: Computer Science (MSc)
Supervisor: Helger Lipmaa
Reviewer: Sven Laur
Defense: 02.06.2016, 09:00, Liivi 2-405A Comprehensive Protocol Suite for Secure Two-Party Computation
Abstract: In some scenarios, a two-party model is a better fit when no natural third party is involved in the application. In this work, we design and implement a full protocol suite for two-party computations on Sharemind, providing an alternative and viable solution in such cases.
Student: Sander Siim
Curriculum: Computer Science (MSc)
Supervisor: Dan Bogdanov, Pille Pullonen
Reviewer: Dominique Unruh
Defense: 06.06.2016, 09:00, Liivi 2-405An improved type system for a privacy-aware programming language and its practical applications
Abstract: he goal of this thesis is to make it easier to add protection domain kinds to the SecreC language by allowing the programmer to define the protection domain kind data types, arithmetic operations and type conversions in the SecreC language without changing the compiler.
Student: Ville Sokk
Curriculum: Computer Science (MSc)
Supervisor: Dan Bogdanov, Jaak Randmets
Reviewer: Vesal Vojdani
Defense: 06.06.2016, 09:00, Liivi 2-405Energy Harvesting in Cooperative Communications
Abstract: Energy harvesting (EH) is a crucial technology for a variety of wireless systems that have limited access to a reliable electricity supply or recharging sources. In this thesis, the design of a multiple access relay system (MARS) using EH is considered.
Student: Akashkumar Rajaram
Curriculum: Cyber Security (MSc)
Supervisor: Nalin Jayakody, Vitaly Skachek
Reviewer: Bin Chen
Defense: 06.06.2016, 09:00, Liivi 2-405Security of Eduroam Passwords
Abstract: The University of Tartu has decided that the university’s eduroam accounts will share the same user credentials as the rest of the university’s services. This could potentially be abused by exploiting weaknesses in wireless security in order to gain access to a user’s university account. The aim of this research was to uncover any such weaknesses.
Student: Raul-Martin Rebane
Curriculum: Computer Science (BSc)
Supervisor: Dominique Unruh
Reviewer: Meelis Roos
Defense: 06.06.2016, 09:00, Liivi 2-405
Applying a Security Testing Methodology: a Case Study
Abstract: This thesis aims to describe and apply a process necessary to verify the security of a web application. A checklist of security requirements was gathered combining OWASP ASVS web application security standard and OWASP Top Ten project.
Student: Karin Klooster
Curriculum: Computer Science (BSc)
Supervisor: Meelis Roos, Margus Freudenthal
Reviewer: Kritjan Krips
Defense: 08.06.2016Word frequency based log analysis
Abstract: The purpose of this bachelor thesis is to explore if you can use word frequency based analysis for log files and find interesting events without knowing the log structure.
Student: Karl Lääts
Curriculum: Computer Science (BSc)
Supervisor: Meelis Roos
Reviewer: Artjom Lind
Defense: 08.06.2016Randomly Distributed PIN Code Input Layout
Abstract: This thesis examines the possibility of reducing the visual security breach of PIN code input by randomising the input field.
Student: Rain Tõugjas
Curriculum: Computer Science (BSc)
Supervisor: Tauno Palts, Kristjan Krips
Reviewer:
Defense: 08.2016Smart Home Hacking
Abstract: This work investigates the security and privacy issues found at an emerging smart home technology such as the CoSSMic platform.
Student: Suela Kodra
Curriculum: NordSecMob (MSc)
Supervisor: Danilo Gligoroski, Marie Moe, Dominique Unruh
Reviewer: Raimundas Matulevičius
Defense: 18.08.2016, 09:30, Liivi 2-403Cache-Timing Techniques: Exploiting the DSA Algorithm
Abstract: This work explains some of the cache-timing techniques commonly used to exploit vulnerable software. Using a particular combination of techniques and exploiting a vulnerability found in the implementation of the DSA signature scheme in the OpenSSL shared library, a cache-timing attack is performed against the DSA’s sliding window exponentiation algorithm.
Student: Cesar Pereida Garcia
Curriculum: NordSecMob (MSc)
Supervisor: Billy Bob Brumley, Dominique Unruh, N. Asokan
Reviewer: Arnis Paršovs
Defense: 26.08.2016, 11:00, Liivi 2-403
Links:
https://comserv.cs.ut.ee/ati_thesis/index.php?year=2016
http://www.cs.ut.ee/sites/default/files/2016/loput88d/Kaitsmiste%20ajakava.pdf