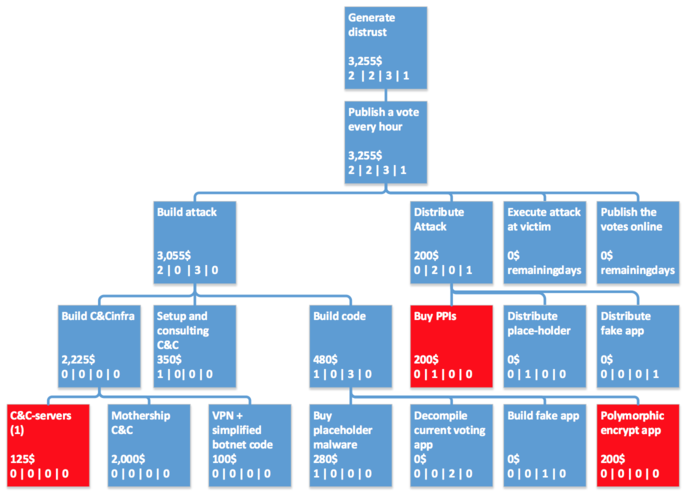
This report analyzes two independent works published in 2014 that model security threats of Estonian i-voting scheme using attack trees. The first one, the master’s thesis of Tanel Torn [11] constructs several realistic attack trees for various types of attacks on Estonian i-voting system and evaluates them using three different state-of-the-art methodologies proposed in attack-tree literature. The second work, the master’s thesis of Ruud Verbij [13], proposes a general framework to allow comparison of different internet voting schemes. Verbij evaluates the proposed framework by applying it on Estonian i-voting protocol.
Despite using different approaches, both Torn and Verbij agree on some of the results. First, they both consider attacks on the Central System to be much more expensive, involving more risk and thus less probable. Second, results of both authors’ analyzes show that revocation attacks are more profitable than vote modification attacks. This in mainly due to the fact that in the former case the attack does not have to go through undetected.
The report has been published for UT course “Research Seminar in Cryptography (MTAT.07.022)”.
Links
https://courses.cs.ut.ee/2014/cryptoseminar/fall/uploads/Main/riivo-report-f14.pdf