We wrote about the case before. Here is a summary of court’s decision:
According to the first-level Harju County Court decision, Mart Pirita (45) was pleaded guilty for disrupting the remote services of Ministry of the Interior (SM). According to the verdict, he used anonymous Tor network to enter multiple wrong passwords for 14 users, thereby blocking their access to the infrastructure.
The actions were qualified according to Penal Code paragraph 207 part 1 for “Illegal interference with or hindering of the functioning of computer systems by way of uploading, transmitting, deleting, damaging, altering or blocking of data”.
Pirita’s attorney Raul Ainla challenged the qualification of the alleged crime. In county court’s opinion, the qualification was correct, since Mart Pirita entered without lawful permission wrong passwords for 14 user accounts, by which their accounts were disabled, interfering the functioning of the computer system for SM employees.
The first-level court’s decision was appealed and District Court of Tallinn made a decision, that it was not possible to certainly establish a connection between Mart Pirita and the attacks.
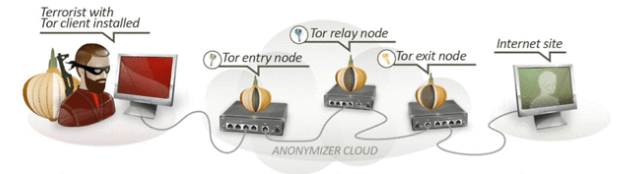
In the initial verdict, it was claimed that the attack was performed through three IP addresses which are known to be Tor exit nodes. Furthermore, it was established that Pirita downloaded Tor software from Debian repository (ftp.ee.debian.org). In addition, according to Pirita’s ISP Elion metadata logs, Pirita was connected to the Tor network approximately at the time of the attacks.
District court judged that the county court has incorrectly evaluated the evidence presented. Namely, the IP addresses, where the attacks were performed from, belong to the Tor exit nodes and thus the attacks were performed through Tor network. However, the county court did not consider the technology of the Tor network. Every connection through Tor network is established via random paths and are encrypted, thus it is impossible to know who is the initial source of the communication and what are the messages. Thus, even though Pirita connected to the Tor network, it is impossible to link him to the attacks from the exit nodes.
Additionally, the prosecuror Piret Paukštys claimed that, since on the Pirita’s hard drive was found file “cached-microdesc-consensus” which included the IP addresses of Tor exit nodes participating in the attack, it proves the connection between Pirita and the exit nodes. However, this claim was found to be false, since the file is a catalog of all public Tor nodes and is included in every Tor installation. Thus, every Tor user possibly could be behind the attack.
According to prosecutor, another evidence pointing to Pirita was that Pirita had Debian Linux installed in his virtual machine and attacker’s user agent “Mozilla/5.0 (Linux; U; Debian Linux; en-US; rv: 1.8.1.12) Gecko/20080201 Firefox/2.0.0.12” presented to the court has Debian Linux operating system in it.
However, Tiit Hallas, the head of information security of SMIT could not provide to the court any log file which backed the claim of this user agent being present. The claimant couldn’t even describe from which log file this user agent was given from and why the logs weren’t presented as evidence.
Finally, the court found that there is a clear discrepancy between the times in the log files provided as evidence. Firstly, according to ftp.ee.debian.org logs, Pirita downloaded Tor software on 17.08.2014 at 00:57. However, the attacks started on 17.08.2014 at 00:14. Elion’s metadata logs show that Pirita connected Tor network after attacks started. Furthermore, an independent expert from Estonian Forensic Science Institute (EKEI) Oliver Olt stated that there are no connections between Elion’s metadata logs and attacks in claimant’s logs. The expert added that he couldn’t explain how the attack could be performed which would correspond to the logs. Thus, by his opinion, the logs rather contradicted the prosecutor’s claim.
It was said that Pirita had motive to perform the attacks as he was fired from SMIT due to loss of trust. However, the management of SMIT acknowledged that he was not the only one to be fired for this reason. There were up to ten people who could have the motive to perform the attacks. Furthermore, the fact that the attacker knew correct access point is not sufficient to claim that it was performed by current or previous employee of SMIT.
Concluding these aspects, the district court decided that the indirect proof was not sufficient to claim the guilt of Pirita with high probability. According to previous National Court decision, if it is possible that there was anyone else who could have performed the attack, then the accused should not be convicted.
The district court reviewed the previous decision and acquitted Pirita. Additionally, he was compensated for the legal fees in the amount of 7500€. The fee for IT expertise was covered by the government. The disk copy of Pirita’s hard disk is to be destroyed to assure the privacy of Pirita.
The prosecutor did not appeal the district court’s decision.
Links:
https://www.riigiteataja.ee/kohtulahendid/detailid.html?id=180104716
http://www.delfi.ee/news/paevauudised/krimi/pevkuri-ja-vaheri-meilikontode-lukustamise-parast-kohtu-all-olnud-mart-pirita-oigeks-moistmine-on-nuud-loplik?id=74558039
http://www.postimees.ee/3149415/it-spetsialist-jai-ministeeriumi-arvutikontode-blokeerimises-suudi