
During the last CCC (31C3), several talks were given which analysed security provided by different mobile operators.
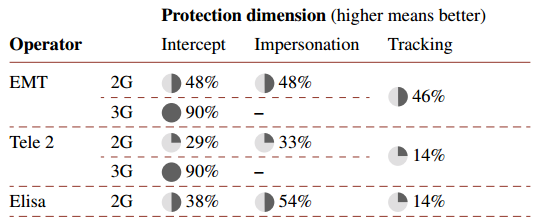
This document provides a security analysis of Estonia’s three mobile networks, based on data collected between October 2012 and December 2014. The analysis is based on data samples submitted to the GSM Map project. It compares implemented protection features across networks. All 3G networks in Estonia implement sufficient 3G intercept protection. None of the networks sufficiently protect against 2G intercept attacks. In all 2G networks, user impersonation is possible with simple tools. All 2G networks in Estonia allow user tracking.
Estonia allows 5 SS7 MAP messages to leak subscriber city location. Estonia allows 2 SS7 MAP messages to leak precise street-level subscriber location (200m). Estonia has 2 operators that leak subscriber keys. Leak of subscriber keys allows an attacker to decrypt calls and SMS of subscriber, by impersonating the network using a fake base station. Estonia has 2 operators susceptible to fraud via change of prepaid/postpaid status.
The EMT seems the most secure, TELE2 the worst secure.
Links:
http://gsmmap.org/assets/pdfs/gsmmap.org-country_report-Estonia-2014-12.pdf
http://ss7map.p1sec.com/country/Estonia/
https://www.youtube.com/watch?v=GeCkO0fWWqc
https://www.youtube.com/watch?v=lQ0I5tl0YLY
Karsten demonstrated in his ccc talk that unbreakable 3G encryption is of no use if mobile operator gives out encryption keys over SS7. In Estonia two mobile operators leak these keys over SS7.